1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
|
import time
import json
import re
from burp import IBurpExtender
from burp import IHttpListener
from burp import IMessageEditorTab
from burp import IMessageEditorTabFactory
from java.io import PrintWriter
class BurpExtender(IBurpExtender, IHttpListener, IMessageEditorTabFactory):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.setExtensionName("Spartan - Wheel king")
self._stdout = PrintWriter(callbacks.getStdout(), True)
callbacks.registerHttpListener(self)
callbacks.registerMessageEditorTabFactory(self)
print '''
[+] #####################################
[+] chao bie ren de
[+] Improve: novy
[+] novy.baklib.com
Readme:
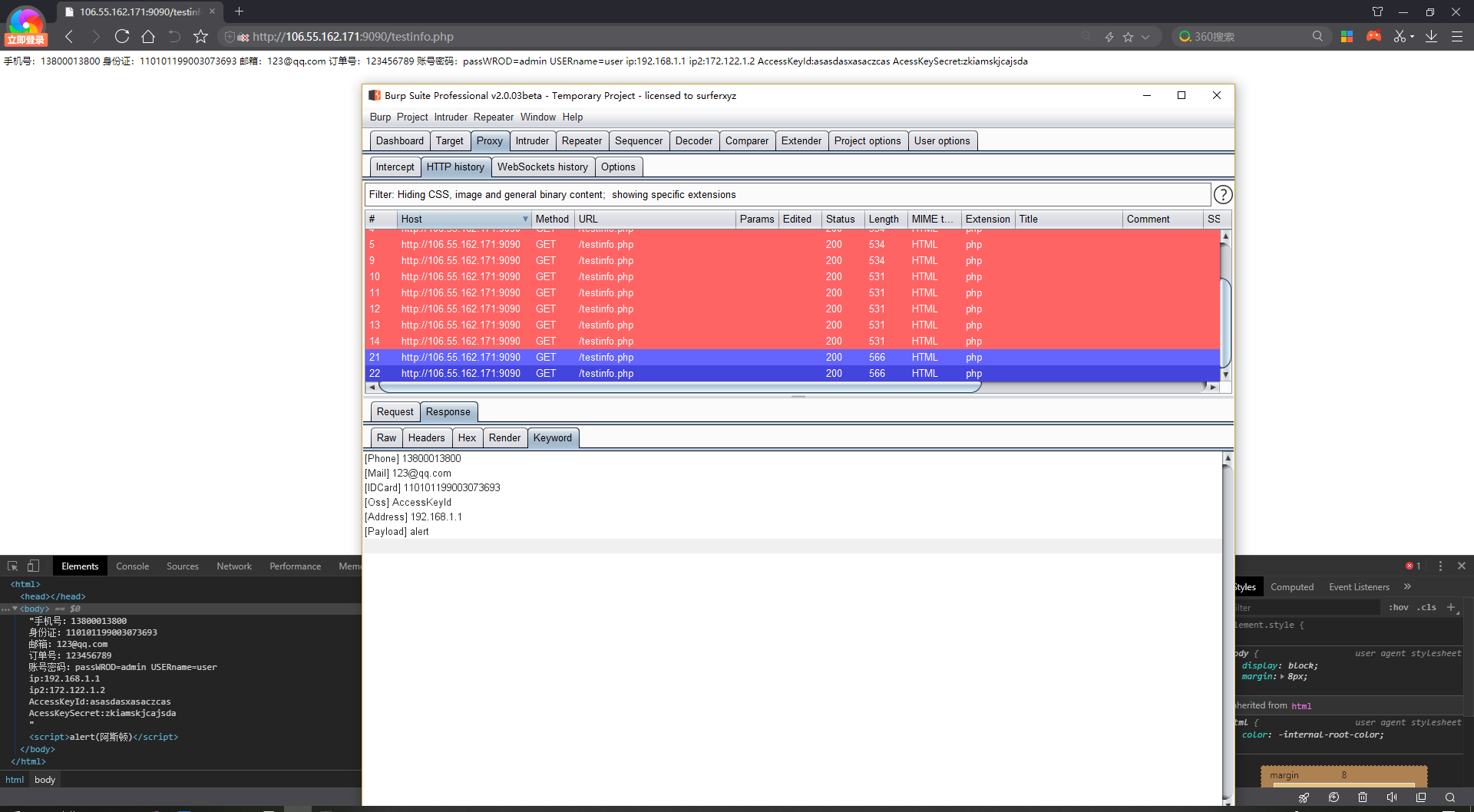
[+] Leakage of regular information such as order number, mobile phone number, account password, ID card, etc.
[+] Yellow represents a single information leak, red represents multiple information leaks
[+] Please add more functions by yourself, support unlimited customization
[+] Not just for mining information leakage.You can create your own plug-in with just a little knowledge of python
[+] #####################################
'''
def createNewInstance(self, controller, editable):
return MarkINFOTab(self, controller, editable)
def processHttpMessage(self, toolFlag, messageIsRequest, messageInfo):
if messageIsRequest:
return
content = messageInfo.getResponse()
r = self._helpers.analyzeResponse(content)
msg = content[r.getBodyOffset():].tostring()
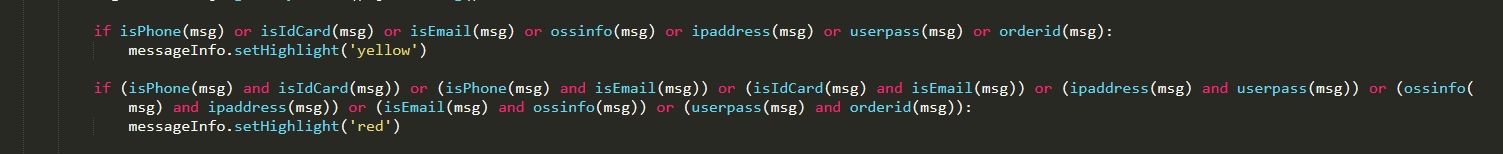
if isPhone(msg) or isIdCard(msg) or isEmail(msg) or ossinfo(msg) or ipaddress(msg) or userpass(msg) or orderid(msg):
messageInfo.setHighlight('yellow')
if (isPhone(msg) and isIdCard(msg)) or (isPhone(msg) and isEmail(msg)) or (isIdCard(msg) and isEmail(msg)) or (ipaddress(msg) and userpass(msg)) or (ossinfo(msg) and ipaddress(msg)) or (isEmail(msg) and ossinfo(msg)) or (userpass(msg) and orderid(msg)):
messageInfo.setHighlight('red')
class MarkINFOTab(IMessageEditorTab):
def __init__(self, extender, controller, editable):
self._extender = extender
self._helpers = extender._helpers
self._editable = editable
self._txtInput = extender._callbacks.createTextEditor()
self._txtInput.setEditable(editable)
self.isInfo = False
def getTabCaption(self):
return "Keyword"
def getUiComponent(self):
return self._txtInput.getComponent()
def isEnabled(self, content, isRequest):
r = self._helpers.analyzeResponse(content)
msg = content[r.getBodyOffset():].tostring()
iphone = isPhone(msg)
email = isEmail(msg)
idcard = isIdCard(msg)
oss = ossinfo(msg)
address = ipaddress(msg)
userp = userpass(msg)
order = orderid(msg)
if not isRequest:
if iphone or email or idcard or oss or address or userp or order:
return True
def setMessage(self, content, isRequest):
if content:
if isRequest:
r = self._helpers.analyzeRequest(content)
else:
r = self._helpers.analyzeResponse(content)
msg = content[r.getBodyOffset():].tostring()
info = ""
iphone = isPhone(msg)
email = isEmail(msg)
idcard = isIdCard(msg)
oss = ossinfo(msg)
address = ipaddress(msg)
userp = userpass(msg)
order = orderid(msg)
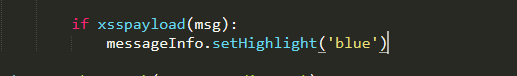
if iphone:
info += '[Phone] ' + ','.join(iphone) + '\n'
if email:
info += '[Mail] ' + ','.join(email) + '\n'
if idcard:
info += '[IDCard] ' + ','.join(idcard) + '\n'
if oss:
info += '[Oss] ' + ','.join(oss) + '\n'
if address:
info += '[Address] ' + ','.join(address) + '\n'
if userp:
info += '[Userp] ' + ','.join(userp) + '\n'
if order:
info += '[Order] ' + ','.join(order) + '\n'
self._txtInput.setText(info)
else:
return False
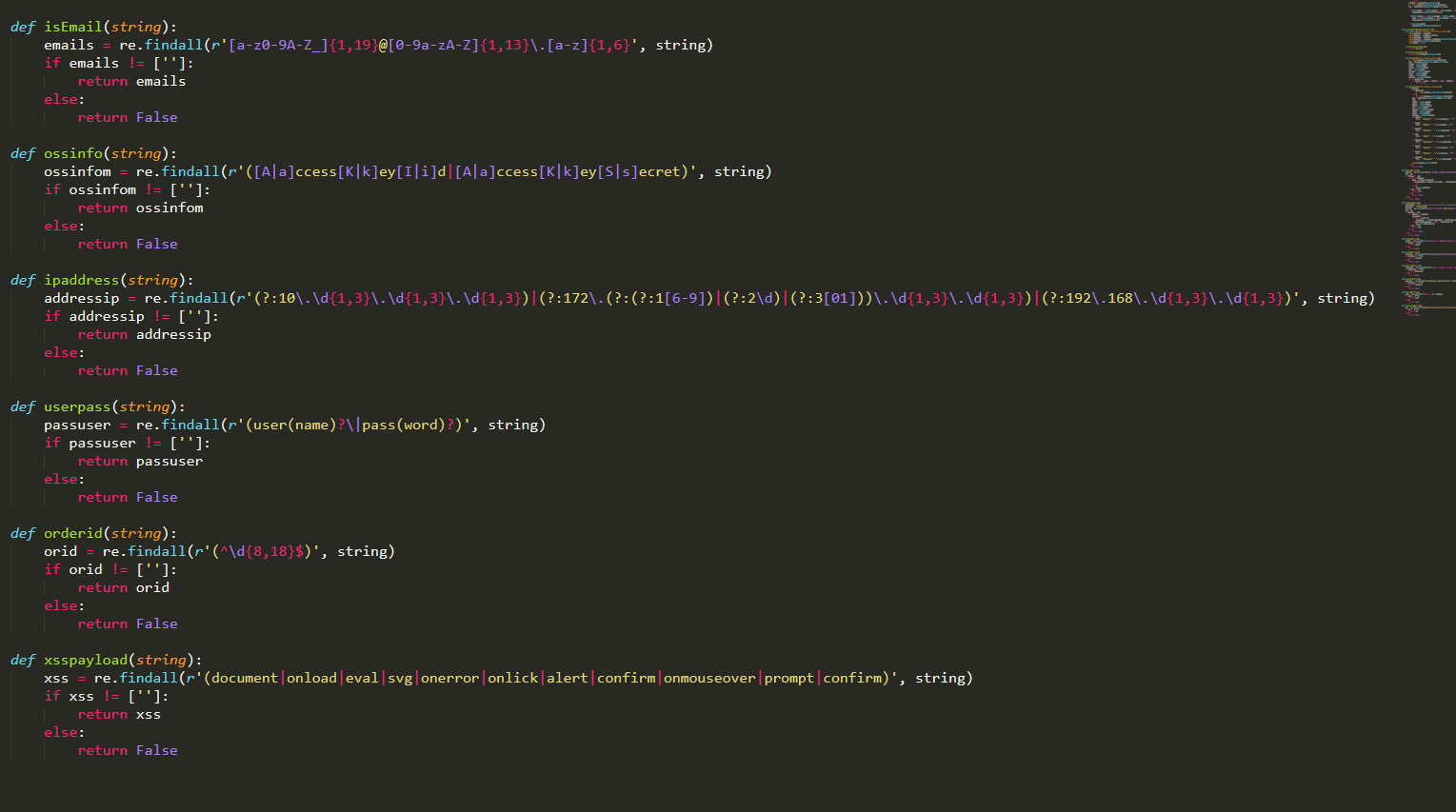
def isPhone(string):
iphones = re.findall(r'((13[0-9]|14[5-9]|15[012356789]|166|17[0-8]|18[0-9]|19[8-9])[0-9]{8})', string)
res = []
if iphones != []:
for i in iphones:
lens = string.find(i[0])
if (string[lens-1:lens].isdigit()) or (string[lens+11:lens+12].isdigit()):
pass
else:
res.append(i[0])
if res != []:
return res
else:
return False
else:
return False
def isIdCard(string):
coefficient = [7, 9, 10, 5, 8, 4, 2, 1, 6, 3, 7, 9, 10, 5, 8, 4, 2]
parityBit = '10X98765432'
idcards = re.findall(r'([1-9]\d{5}[1-9]\d{3}((0\d)|(1[0-2]))(([0|1|2]\d)|3[0-1])((\d{4})|\d{3}[xX]))', string)
res = []
if idcards != []:
for idcard in idcards:
sumnumber = 0
for i in range(17):
sumnumber += int(idcard[0][i]) * coefficient[i]
if parityBit[sumnumber % 11] == idcard[0][-1]:
res.append(idcard[0])
if res != []:
return res
else:
return False
else:
return False
def isEmail(string):
emails = re.findall(r'[a-z0-9A-Z_]{1,19}@[0-9a-zA-Z]{1,13}\.[a-z]{1,6}', string)
if emails != ['']:
return emails
else:
return False
def ossinfo(string):
ossinfom = re.findall(r'([A|a]ccess[K|k]ey[I|i]d|[A|a]ccess[K|k]ey[S|s]ecret)', string)
if ossinfom != ['']:
return ossinfom
else:
return False
def ipaddress(string):
addressip = re.findall(r'(?:10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(?:172\.(?:(?:1[6-9])|(?:2\d)|(?:3[01]))\.\d{1,3}\.\d{1,3})|(?:192\.168\.\d{1,3}\.\d{1,3})', string)
if addressip != ['']:
return addressip
else:
return False
def userpass(string):
passuser = re.findall(r'(i?)\S.*[user]', string)
if passuser != ['']:
return passuser
else:
return False
def orderid(string):
orid = re.findall(r'(^\d{8,18}$)', string)
if orid != ['']:
return orid
else:
return False
|