Springboot devtools <=2.6.4 rce
Devtools is a hot deployment tool of spring boot. It can automatically load projects without manually restarting the spring boot application. During the development process, if we modify some java files, we may need to restart the project to view the modified results. If spring boot devtools is used, devtools will automatically restart the server for you when there are file changes in the classpath (Baidu.com’s introduction, in fact, you can customize the path according to your own situation).
First, look at the configuration information of devtools:
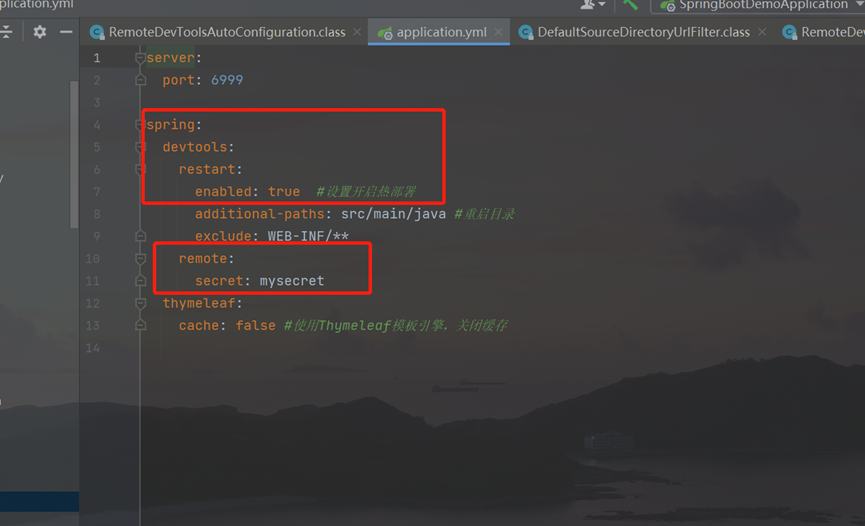
Because all automatic configurations of springboot are performed by xxxautoconfiguration, it is known that:
jetbrains://idea/navigate/reference?project=spring-boot-demo&path=~\.m2\repository\org\springframework\boot\spring-boot-devtools\2.6.4\spring-boot-devtools-2.6.4.jar!\org\springframework\boot\devtools\autoconfigure\RemoteDevToolsAutoConfiguration.class
is the automatic configuration class of devtools
This is for spring devtools. remote. Implementation of secret configuration.
View the process, first pass the values of secretheadername and ‘secret’ into the httpheaderaccessmanager class for processing:
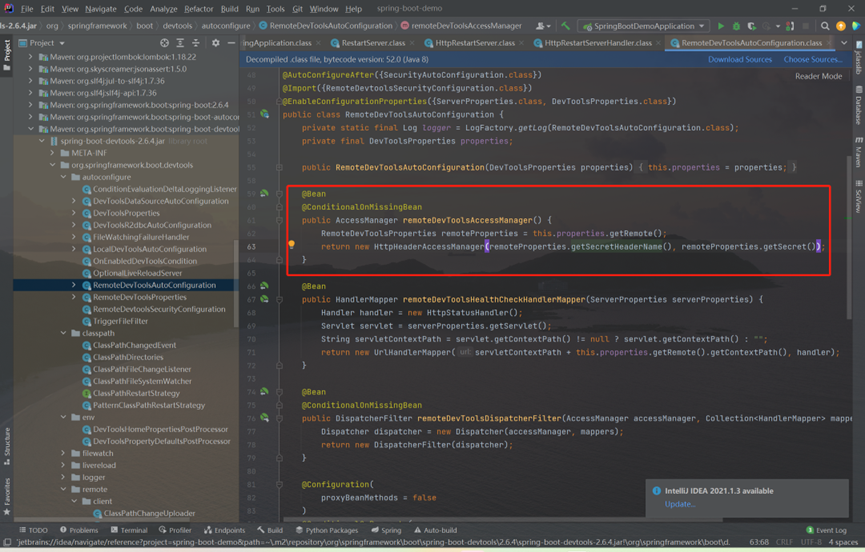
Follow up httpheaderaccessmanager class:
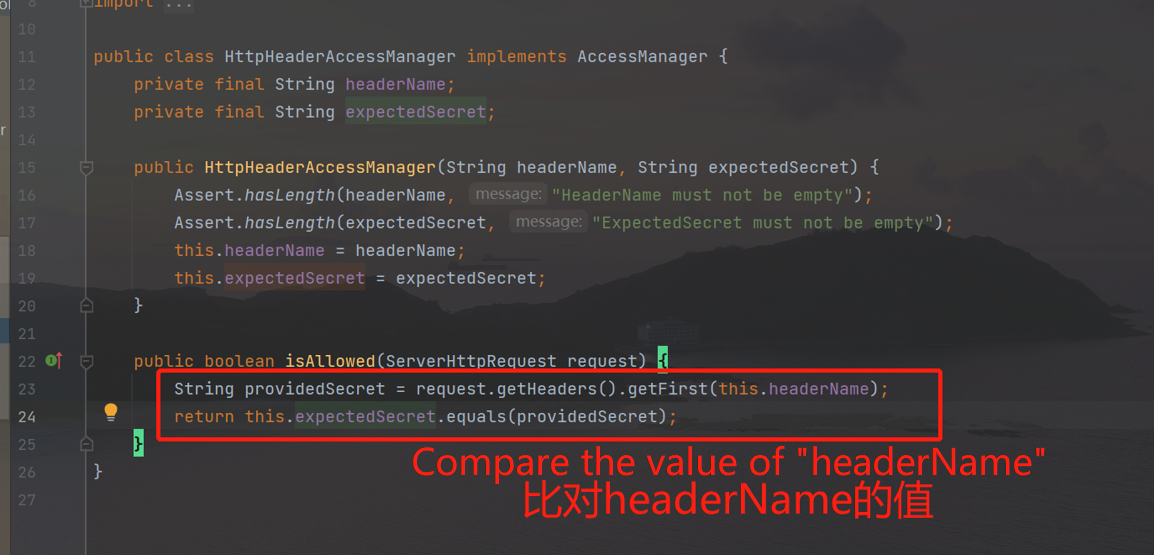
In this class, a parameter HeaderName in the request header will be obtained for comparison. If the value of HeaderName is inconsistent with expectedsecret, 403 will be reported:
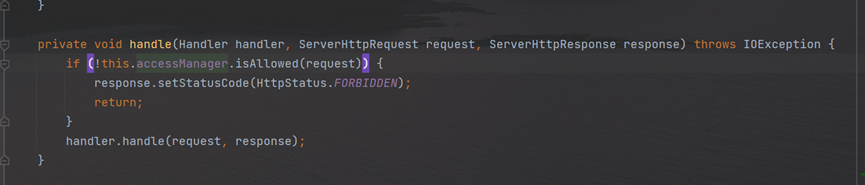
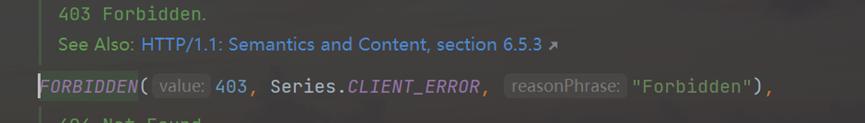
return RemoteDevToolsAutoConfiguration
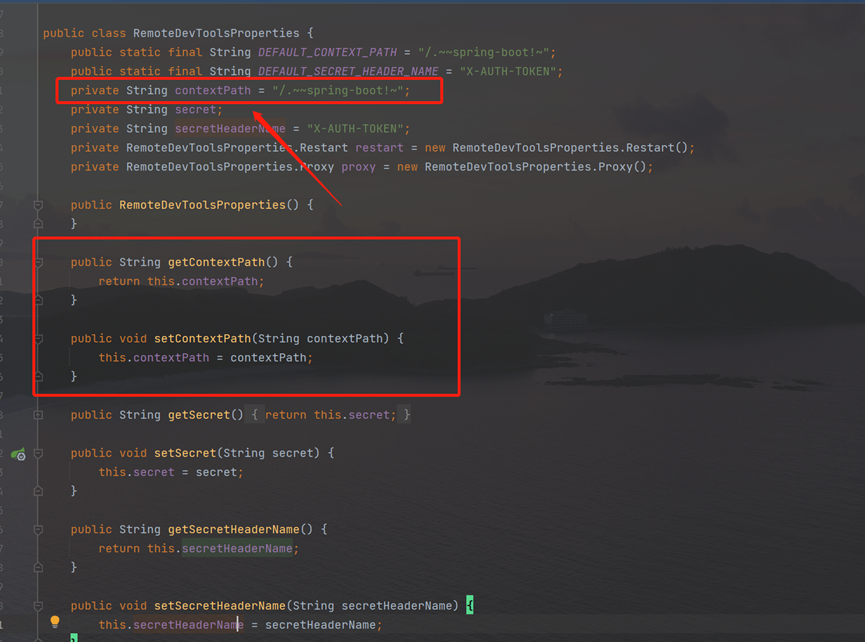
Follow up DevToolsPropertiesclass see SecretHeaderName、Secret:
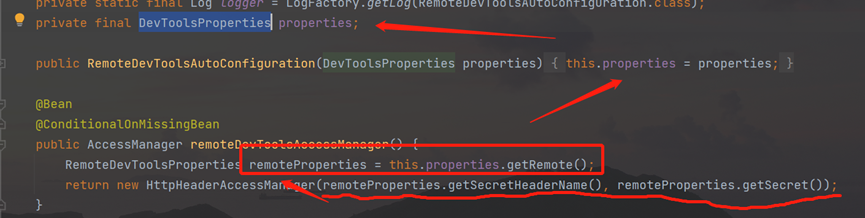
jetbrains://idea/navigate/reference?project=spring-boot-demo&path=~\.m2\repository\org\springframework\boot\spring-boot-devtools\2.6.4\spring-boot-devtools-2.6.4.jar!\org\springframework\boot\devtools\autoconfigure\DevToolsProperties.class
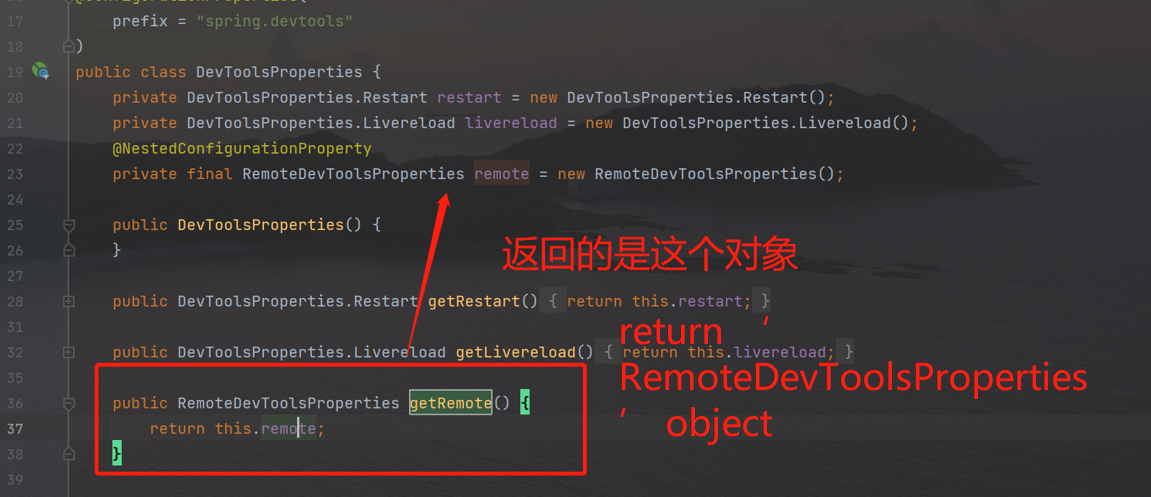
Follow up RemoteDevToolsProperties,in the getsecretheadername method,x-auth-token is returned, that is, the HTTP header has an x-auth-token header.
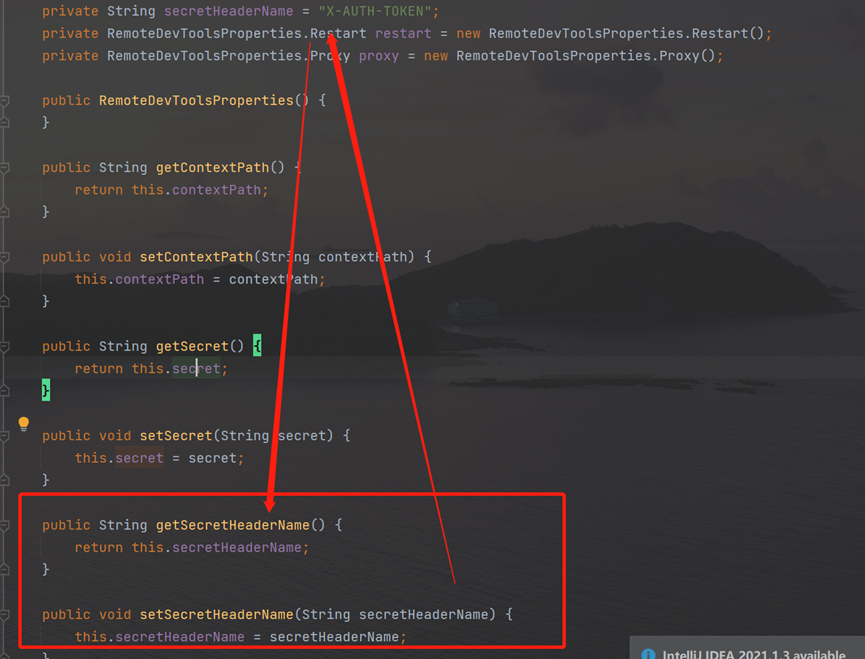
the x-auth-token value
getsecret is obtained from the configuration file:
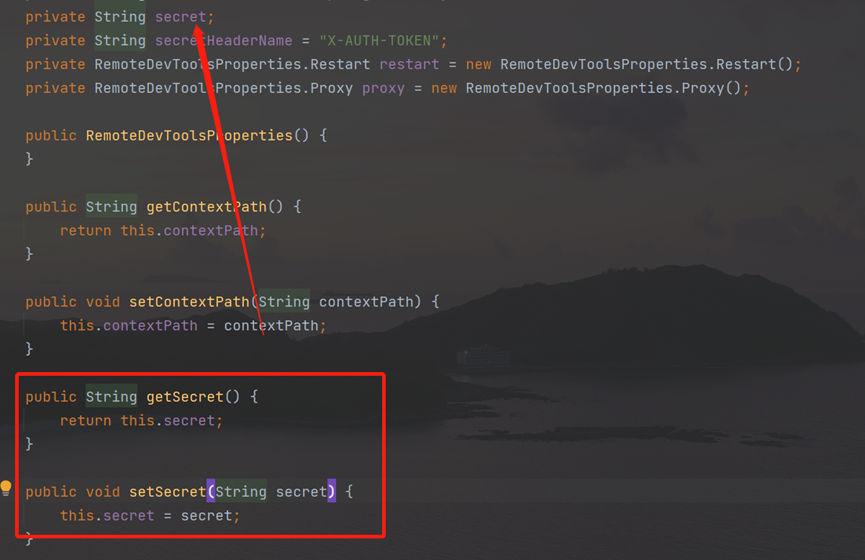
Returning to remotedevtoolsaccessmanager, the httpheaderaccessmanager object returns the verification result of x-auth-token: Secret.
Continue to see vulnerabilities trigger key locations.
This part belongs to the remoterestartconfiguration static class, which is the devtools configuration implementation class:
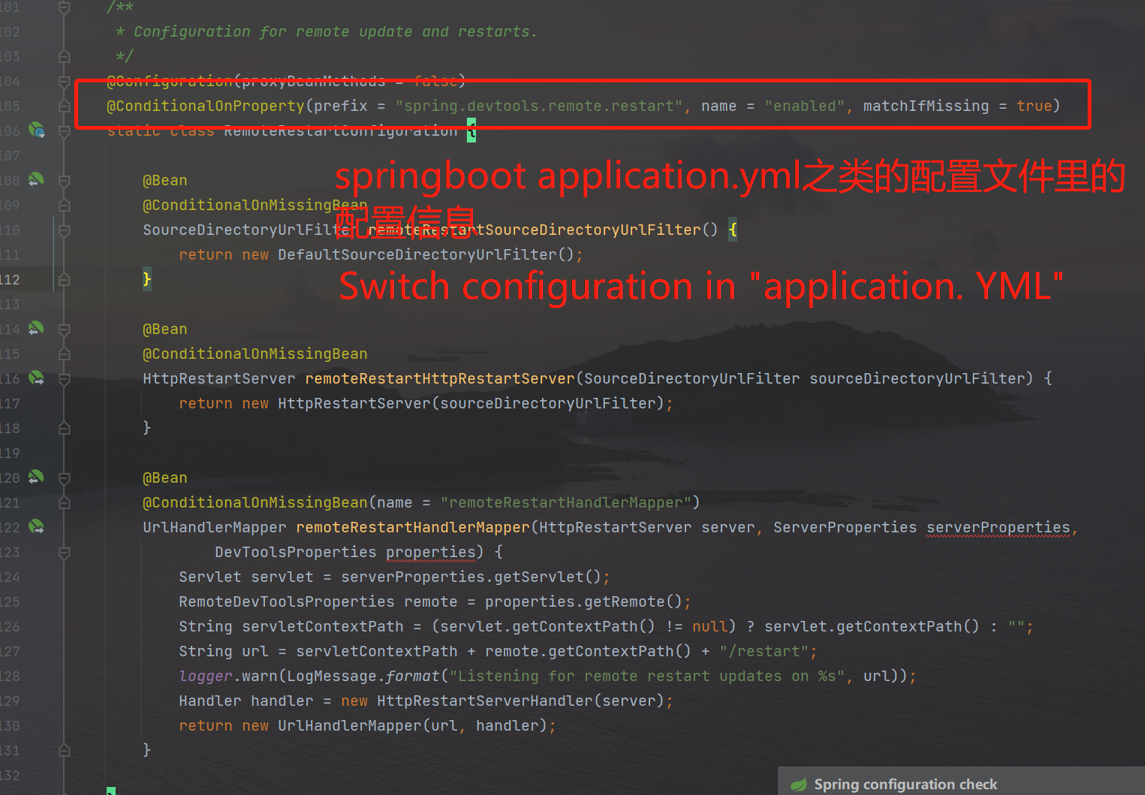
View the remoterestarthandlermapper method
First, see to properties.getRemote(),follow up the devtoolsproperties class:
jetbrains://idea/navigate/reference?project=spring-boot-demo&path=~\.m2\repository\org\springframework\boot\spring-boot-devtools\2.6.4\spring-boot-devtools-2.6.4.jar!\org\springframework\boot\devtools\autoconfigure\DevToolsProperties.class
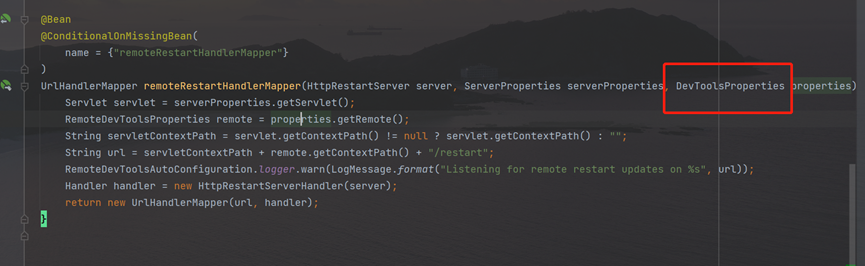
The getremote method returns the remotedevtoolsproperties object
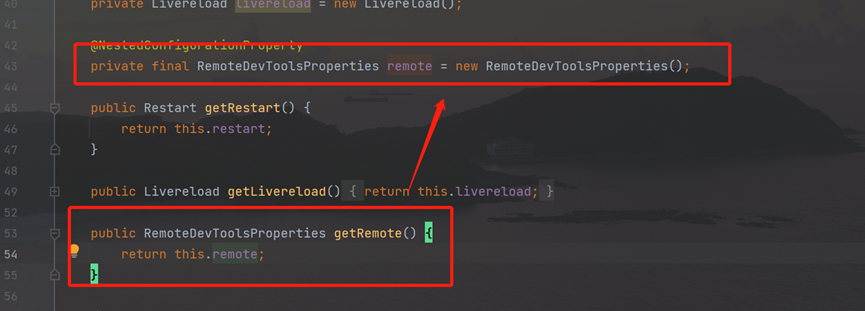
Follow up remotedevtoolsproperties object
This class returns various corresponding property values:
The getcontextpath method returns the URL in the remoterestarthandlermapper method:
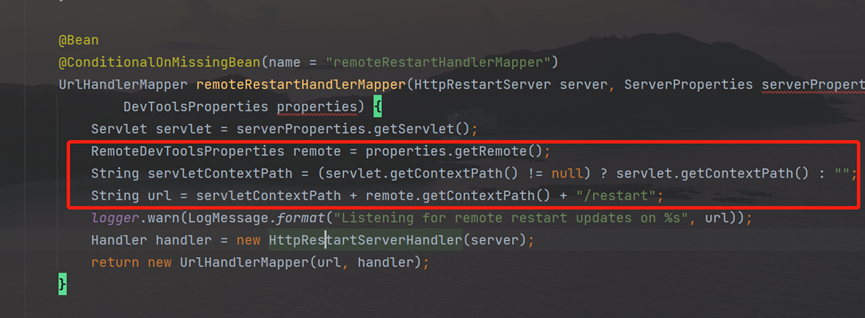
The URL is /~~ spring-boot!~/ restart.
Then continue to watch httprestartserverhandler
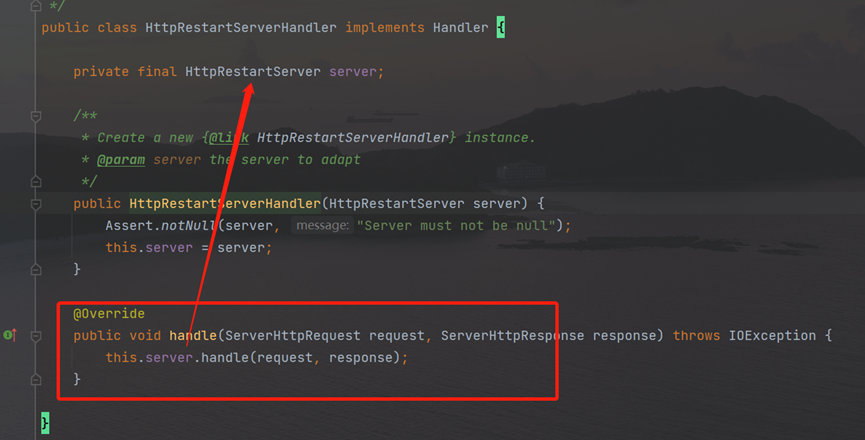
Follow up HttpRestartServer class:
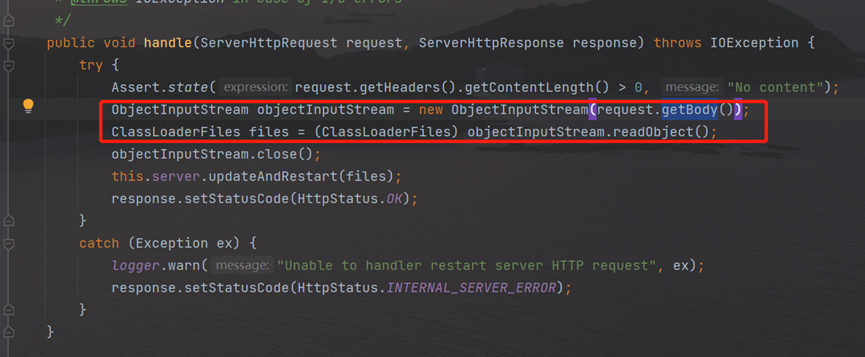
In this class’s Handle method, obtain the request encapsulated as ObjectInputStream object, and then use ObjectInputStream’s ReadObject method,since the request is controllable, the vulnerability is formed.
Verify it:
Construct the request based on the analysis:
1 | |
Dependency:
1 | |
idea will import 2.6.4
Enable remote hot deployment in normal configurationapplication.yml configuration:
1 | |
pom.xml configuration::
1 | |
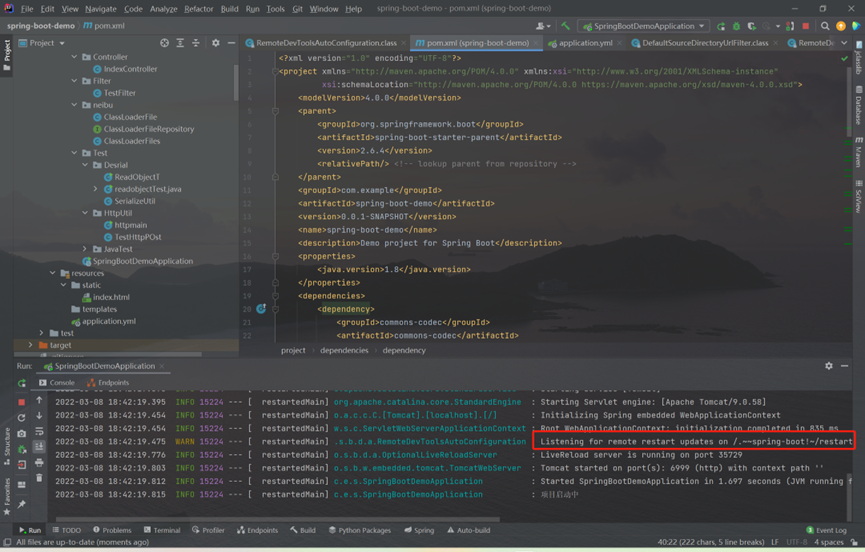
There will be a prompt after the project is started
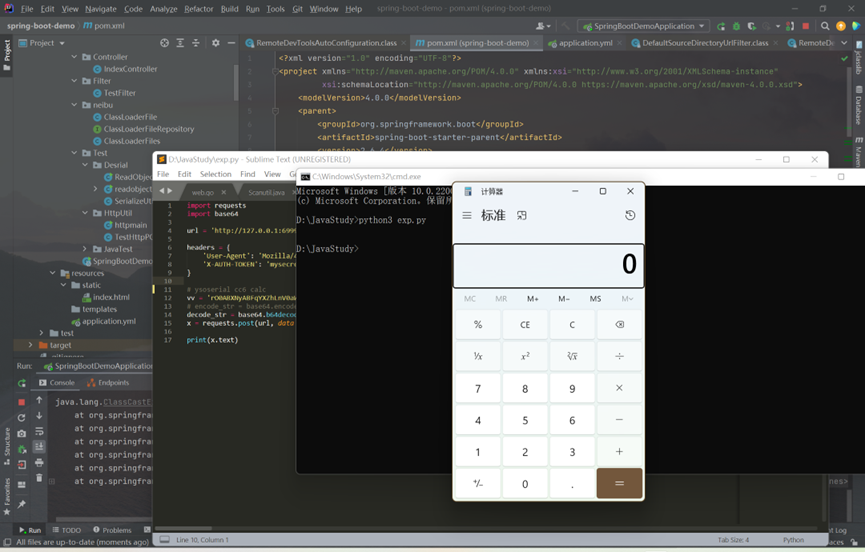
use python writes a PoC to send data
Send the serialized malicious data to the target to trigger:
I found the vulnerability and contacted the spring, but the spring thought they explained the problem in the document, and suggested that the developer change <excludedevtools> false </excludedevtools> to true before releasing the formal environment, so that the production environment will not enable devtools, so it is not a vulnerability.
But I still think this is a risk. I suggest rewriting resolveclass and setting a deserialized object type of white list to avoid malicious deserialization.
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
