tapestry反序列化 CVE-2021-27850分析
漏洞最早可以追溯到<5.3.6版本的tapestry
触发点在FROM类,该类专门用于处理表单
tapestry-core/src/main/java/org/apache/tapestry5/corelib/components/Form.java
首先有两个注意的地方
第一个地方:
表单在点击按钮后会出现一个值为t:submit的name属性,待会会有针对这个的判断
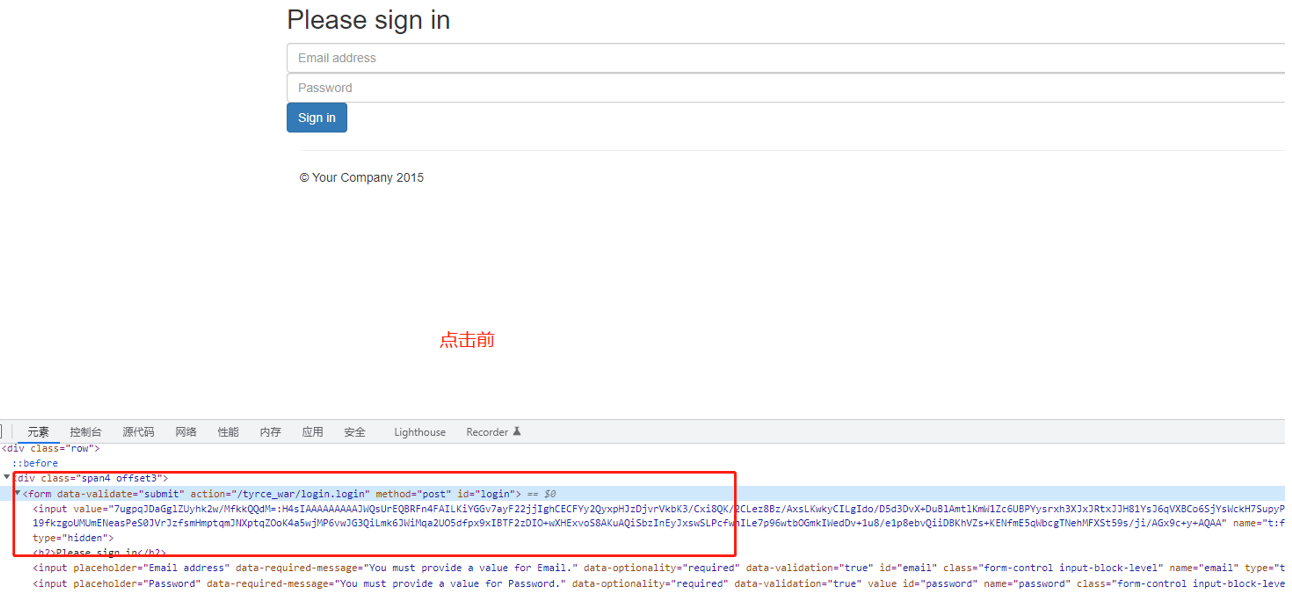
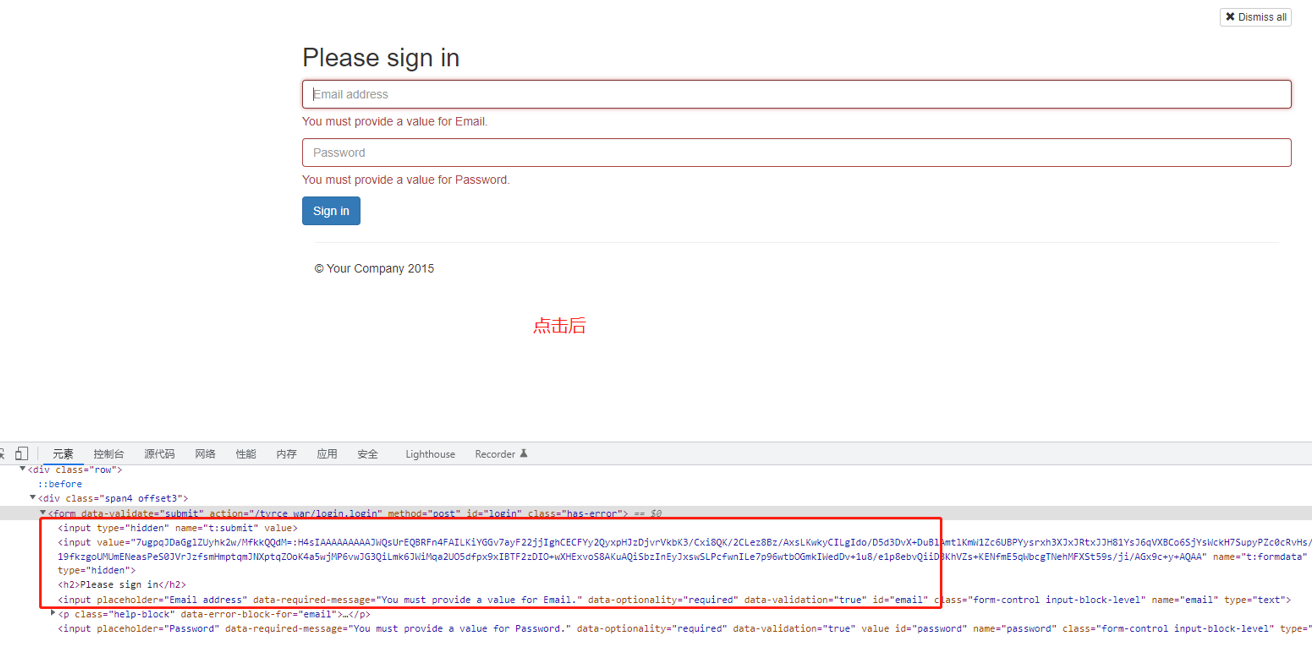
第二个地方:
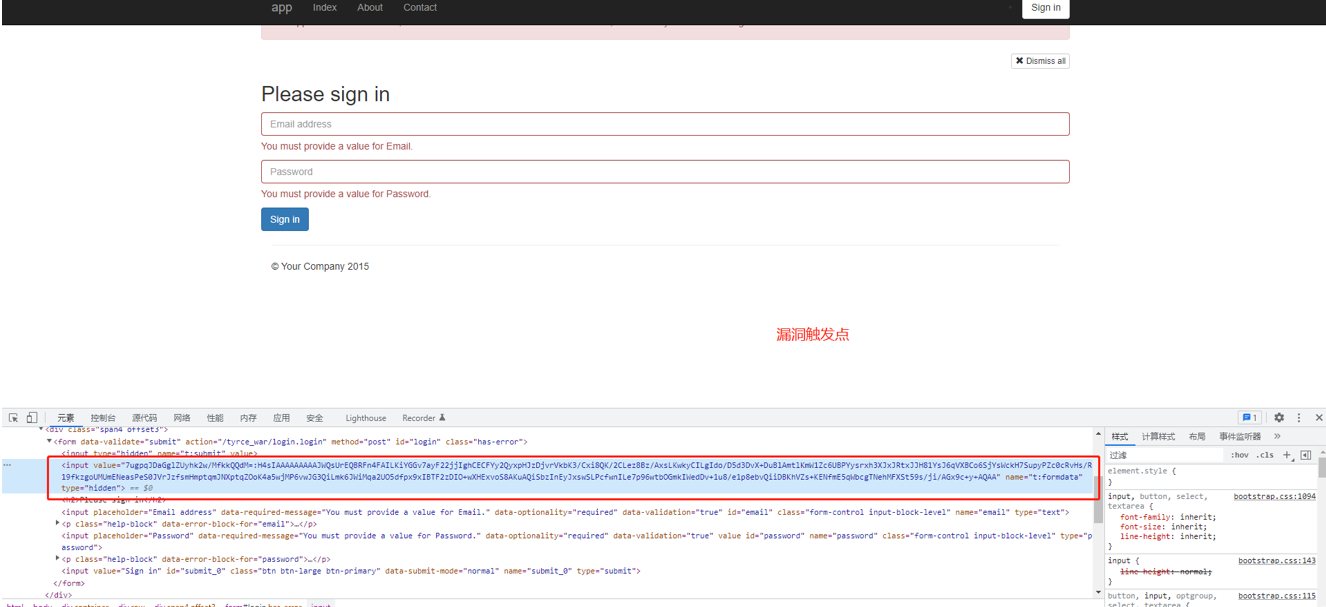
将断点打在onAction方法查看事件处理流程
走到if (this.isFormCancelled()) ,根据返回的布尔类型来进入相应的处理
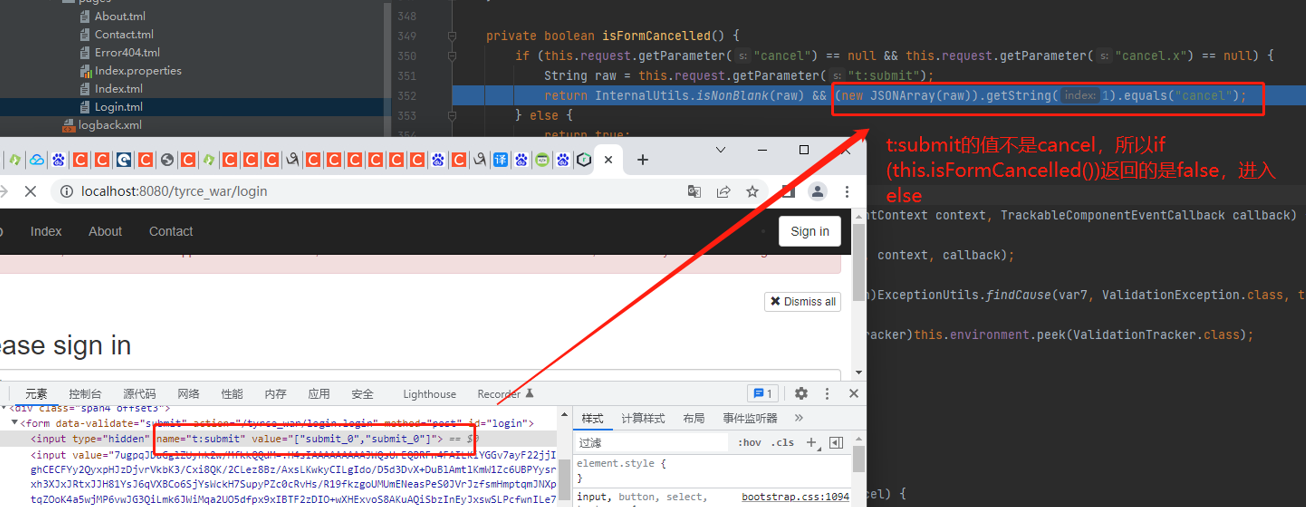
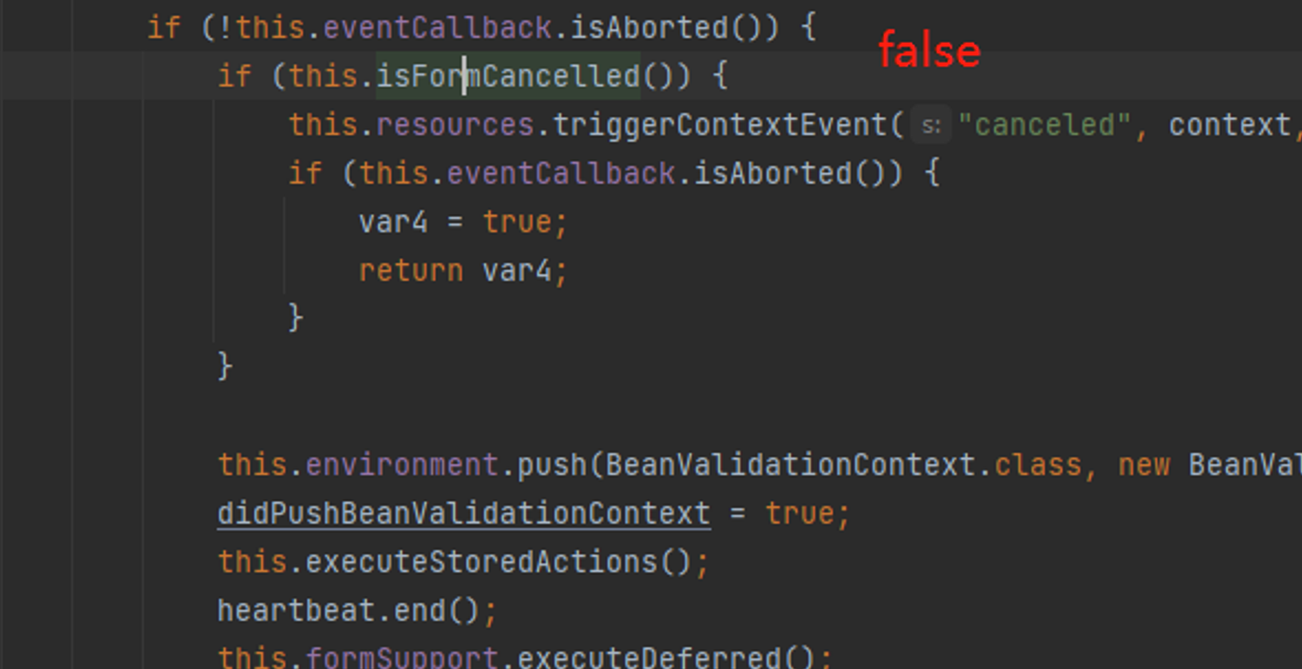
走到this.executeStoredActions();在该方法中会获取t:fromdata的值来进行处理
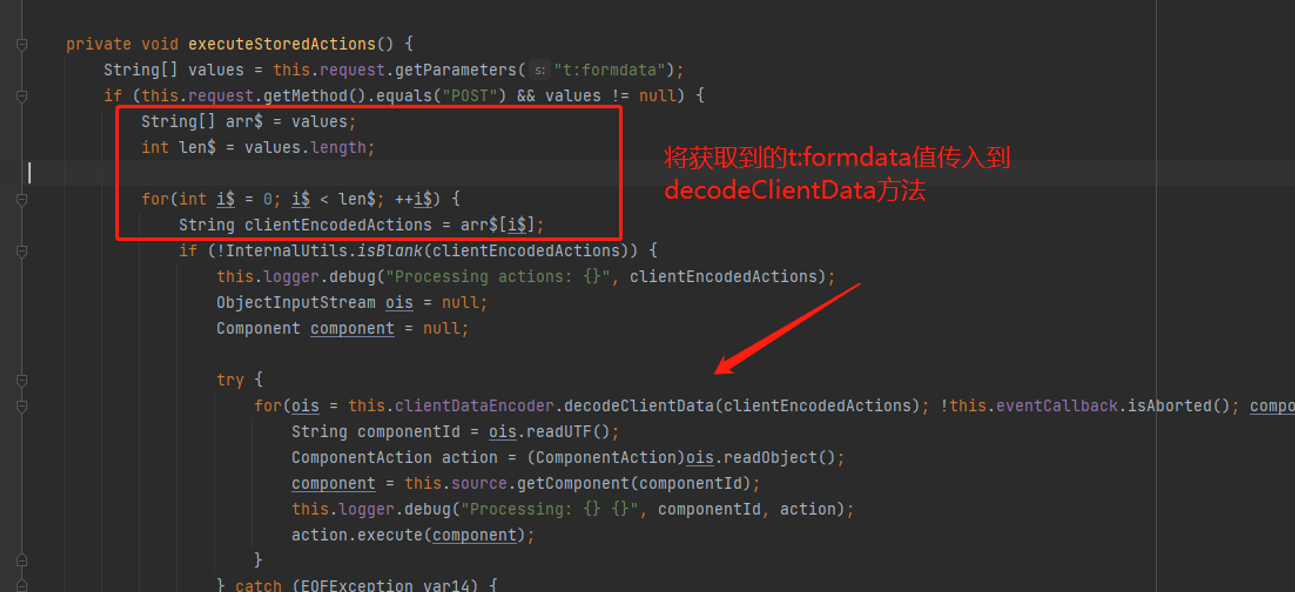
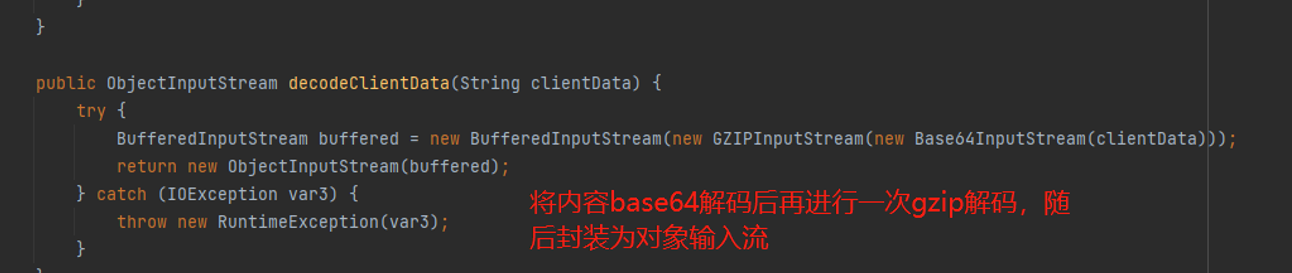
跟进decodeClientData
tapestry-core/src/main/java/org/apache/tapestry5/internal/services/ClientDataEncoderImpl.java
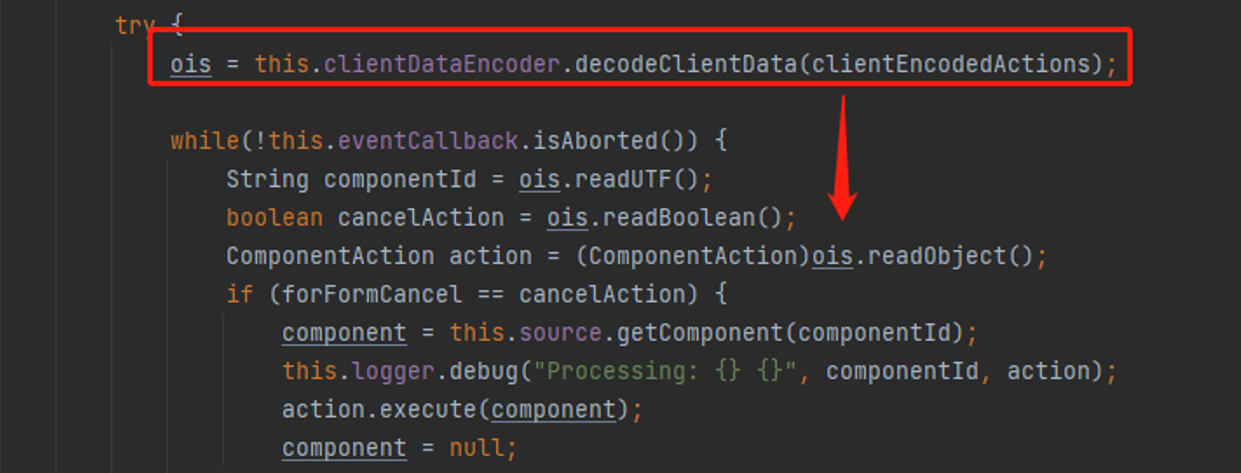
最后进行反序列化,漏洞触发
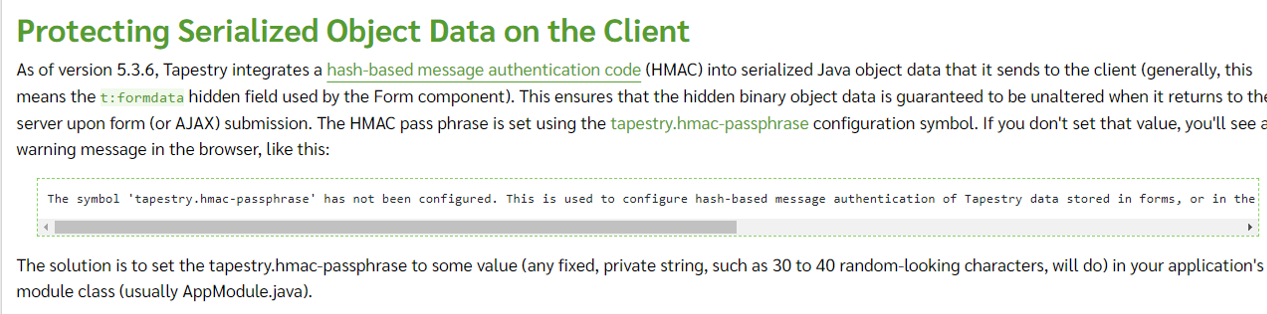
官方在5.3.6及以后(5.4.0-5.6.1,5.7.0)的版本中并没有针对readObject进行修复,而是增加了HMAC,用途是对序列化的数据进行加密,Tapestry的所有序列化数据传输都需要使用HMAC Key进行加密,具体见
https://tapestry.apache.org/security.html
官方原本想的是通过校验签名来防止数据被篡改,然而即使使用HmacSHA1算法加密也不能保证反序列化不被利用,这时候就要说到Tapestry 的另一个漏洞:Tapestry 任意文件下载(CVE-2019-0195),详见https://www.modb.pro/db/113860,可以通过搭配文件下载下载包含有硬编码密钥的class来利用反序列化漏洞,原理类似于shiro的rememberMe反序列化
继续看看加了加密机制后的tapestry,这里用的是5.4.0
直接看到decodeClientData方法
在decodeClientData方法中处理t:formdata的值
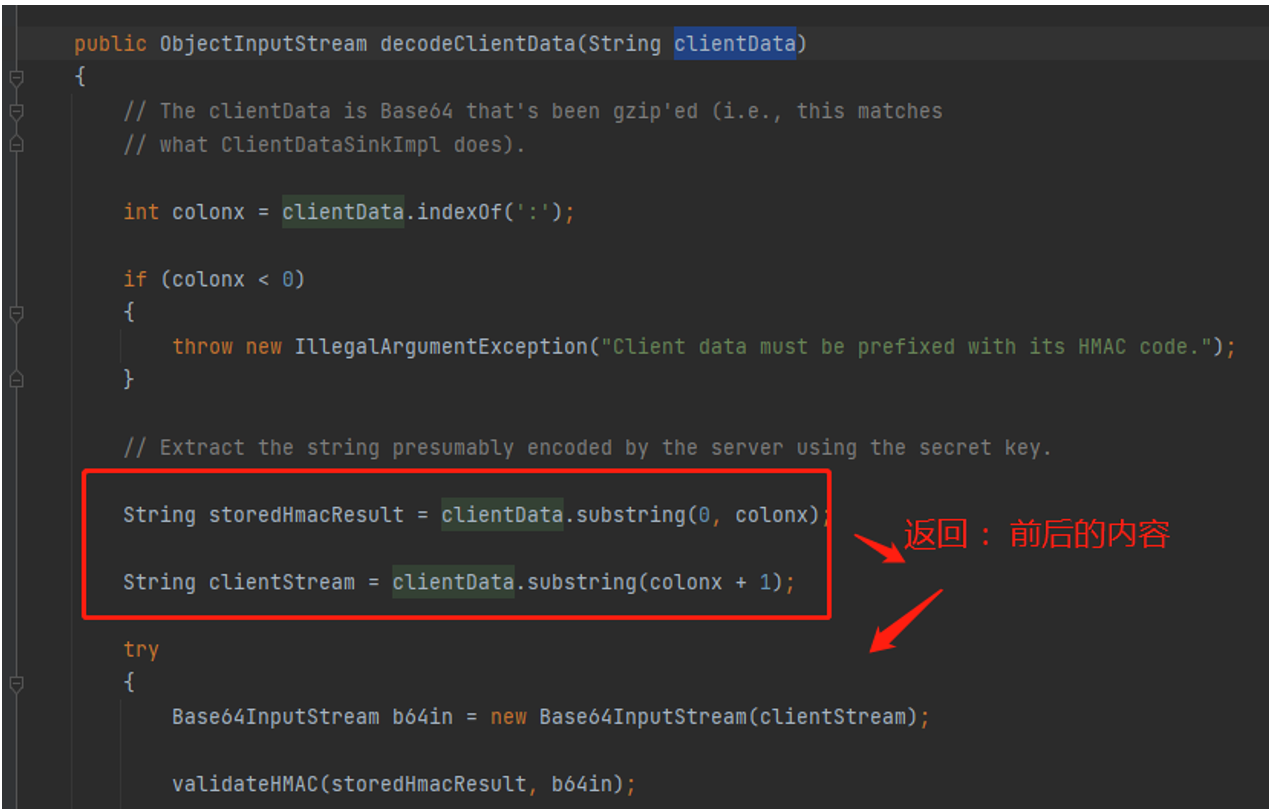
取得clientStream后进行base64解码
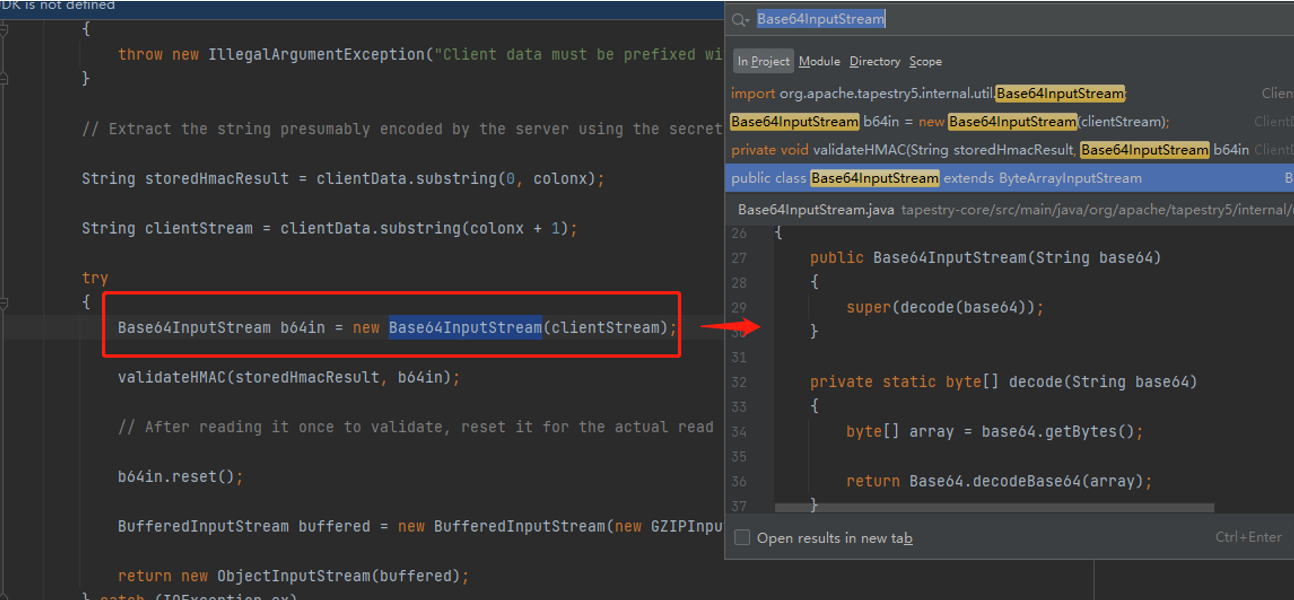
在经过validateHMAC方法校验签名无误后,把base64解码后的clientStream再进行一次gzip解码,随后将解码后的clientStream封装成对象输入流
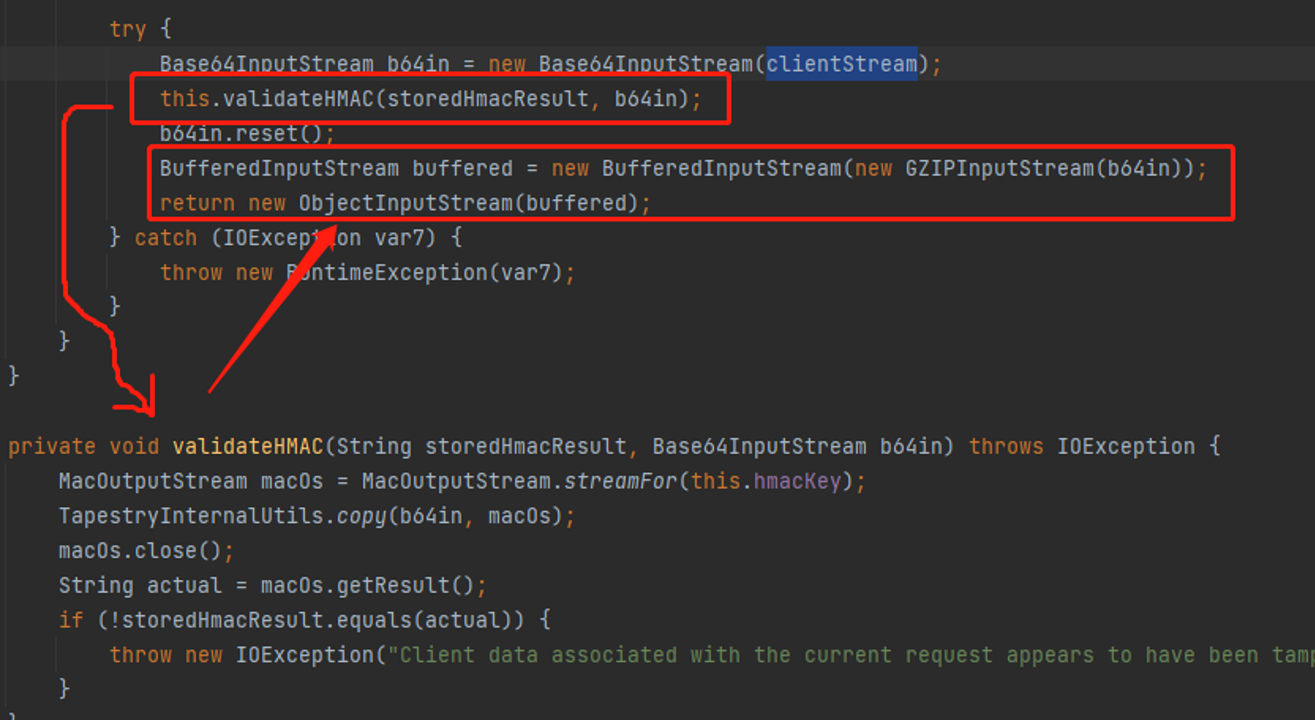
再进行反序列化操作,漏洞产生
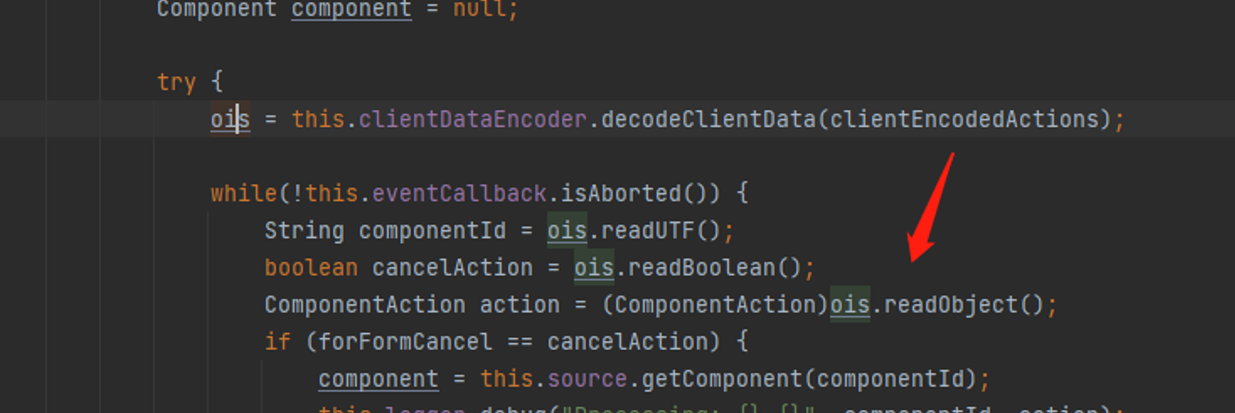
可以看到在decodeClientData方法中加了对t:fromdata内容的处理,且加了一个ois.readBoolean()
在validateHMAC方法中,this.hmackey即包含有HmacSHA1加密算法的SecretKeySpaec对象
tapestry-core/src/main/java/org/apache/tapestry5/internal/services/ClientDataEncoderImpl.java
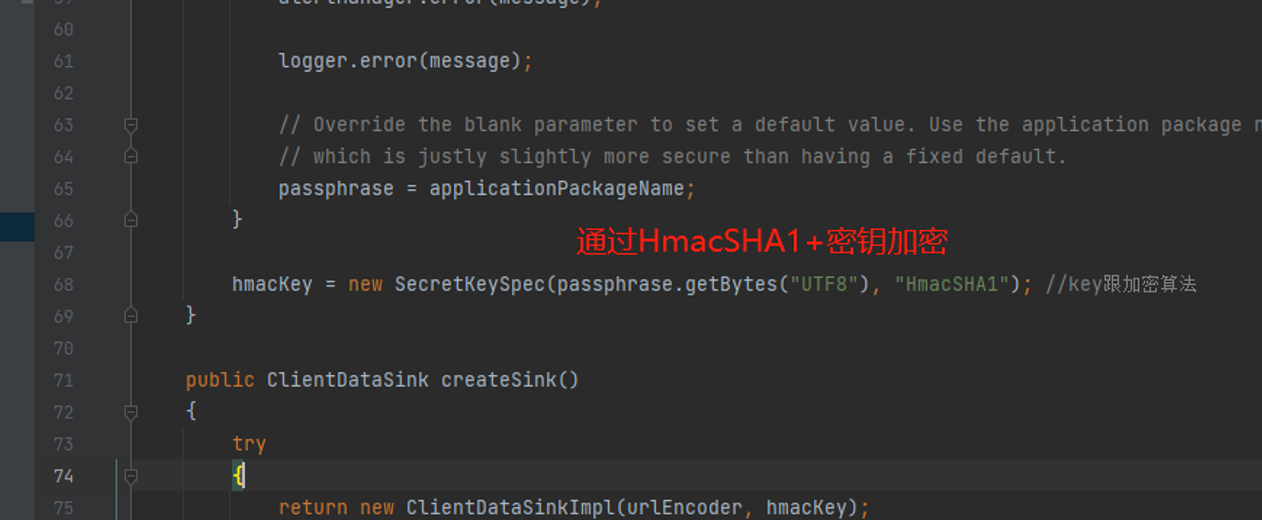
passphrase来自@Symbol
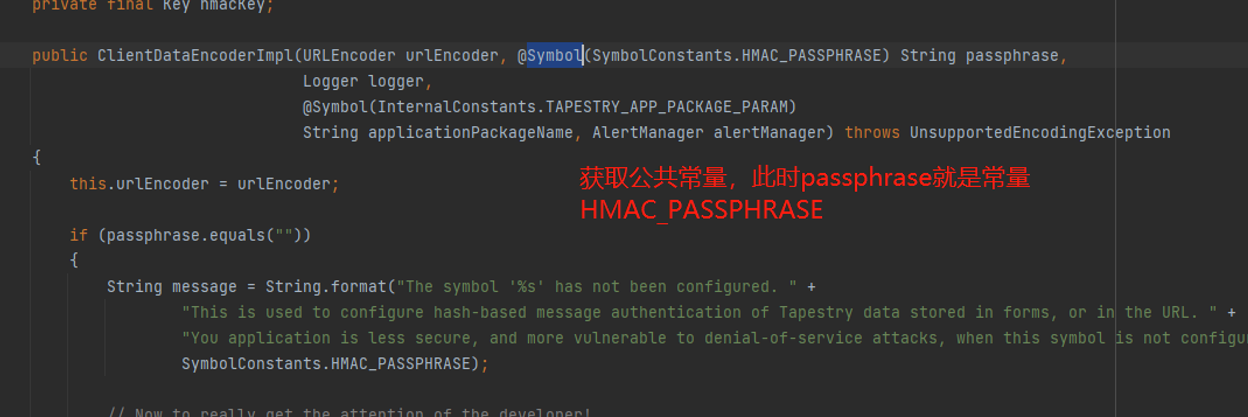
HMAC_PASSPHRASE即加密密钥
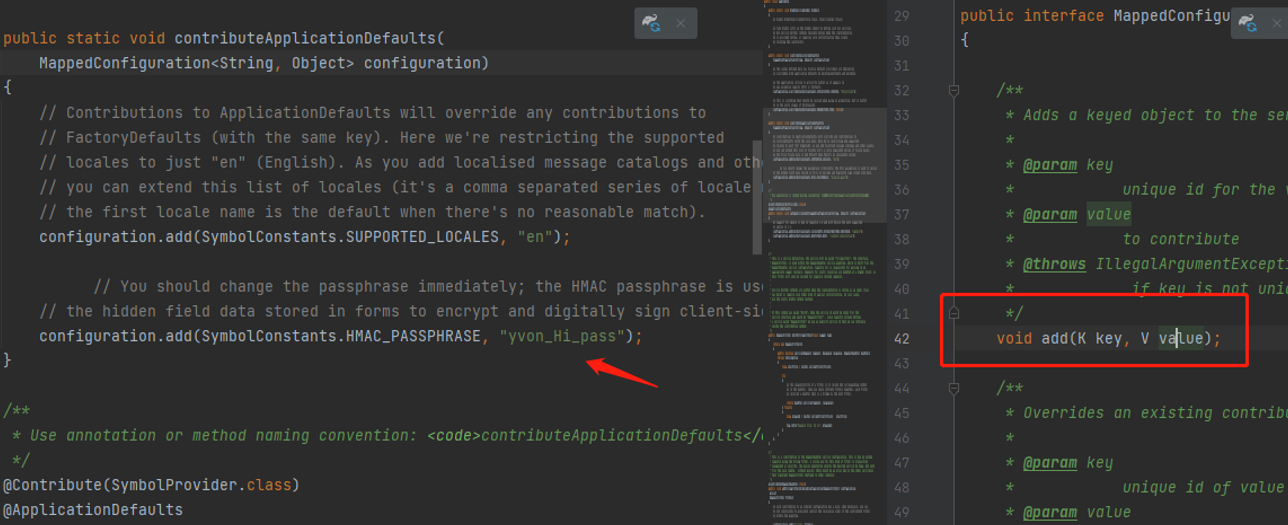
总结其编码模式:
1 | |
根据网上的文章改造一下能用的 ,在ysoserial中引用一下5.3.6版本的Tapestry依赖,在payload目录中新建一个TapestryrcePOC 类,使用CommonsCollections6来触发漏洞
1 | |
生成payload后,可以直接将payload复制到表单请求
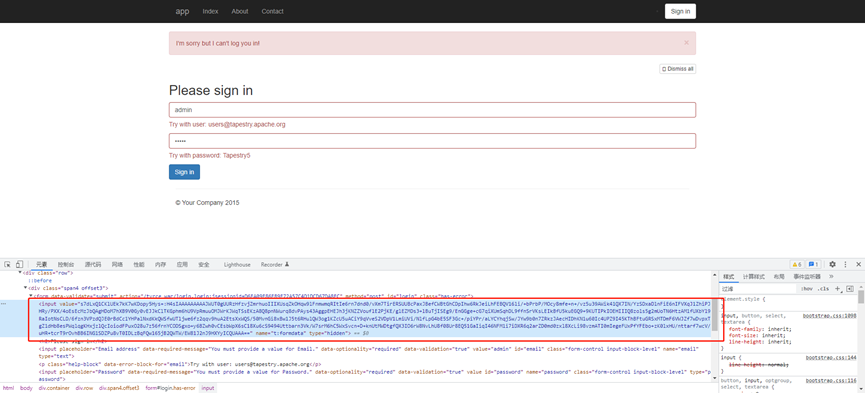
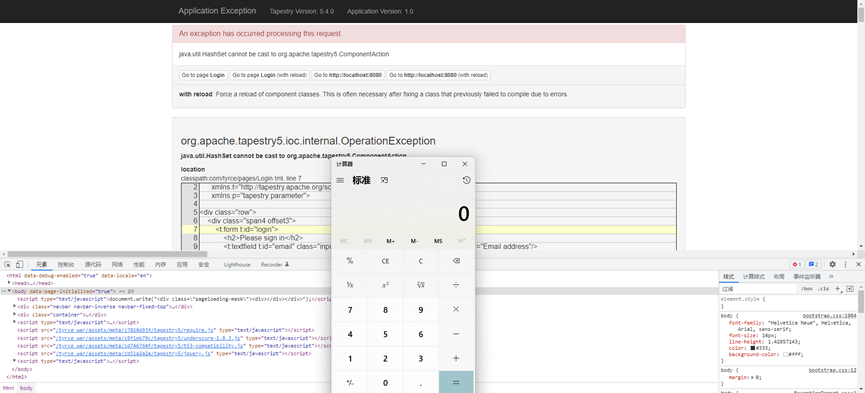
参考
https://www.imangodoc.com/23732.html
https://blog.csdn.net/wyswlp/article/details/6704545
https://blog.csdn.net/u012749355/article/details/38440613?locationNum=5&fps=1
https://tapestry.apache.org/security.html
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
