Log4j1.2.17 RCE
Vulnerability discovered in early 2020.
After reading CVE-2019-17571, I found that there is another vulnerability under chainsaw,there is a deserialization process for socket data in the LoggingReceiver class, and the lack of verification leads to the occurrence of vulnerabilities
Vulnerability analysis:
Set the listening port in the setupReceiver method on line 133 of src/main/java/org/apache/log4j/chainsaw/Main.java
1 | |
Then go to the LoggingReceiver class to process related connection information:
1 | |
Follow up LoggingReceiver class,get the data in the run method, encapsulate the mClient data into the ObjectInputStream object, Deserializing the ois object triggers the vulnerability:
src/main/java/org/apache/log4j/chainsaw/LoggingReceiver.java
1 | |
Vulnerability verification:
Start the visualization component
1 | |
Sending the payload generated by ysoserial (https://github.com/angelwhu/ysoserial) to port 4445 of the target can trigger the vulnerability.
eg, generate malicious data exp.ser first:
1 | |
Write a python socket client after generating the data:
exp.py:
1 | |
running exp.py can trigger the vulnerability.
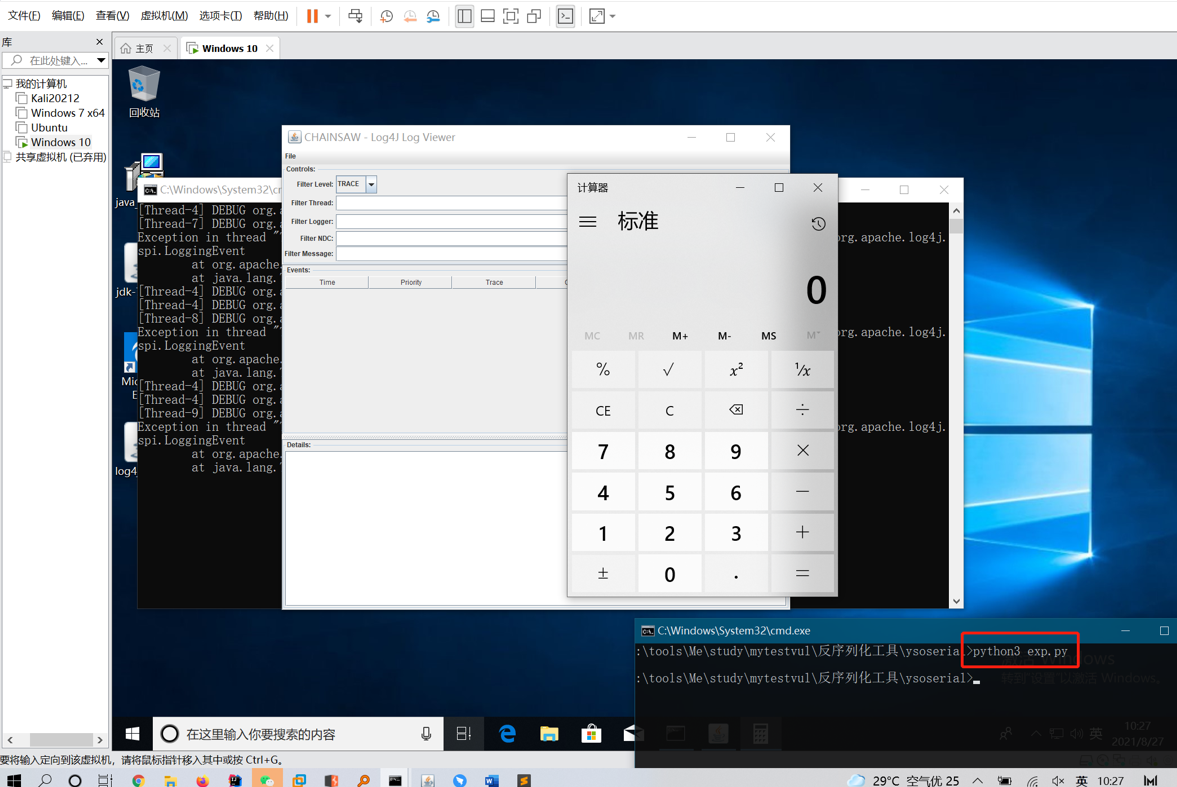
OR
Web demo:
1 | |
When you run the above demo, you will be prompted:
1 | |
It will prompt to wait for a connection. At this time, sending malicious serialized data to port 4445 will trigger the vulnerability.
声明:
本文章用于学习交流,严禁用于非法操作,出现后果一切自行承担,阅读此文章表示你已同意本声明。
Disclaimer:
This article is for study and communication. It is strictly forbidden to use it for illegal operations. All consequences shall be borne by yourself. Reading this article means that you have agreed to this statement.
